Packet Filtering
| Capture Filters | This type of filter is used to save only a specific part of the traffic. It is set before capturing traffic and not changeable during the capture. |
| Display Filters | This type of filter is used to investigate packets by reducing the number of visible packets, and it is changeable during the capture. |
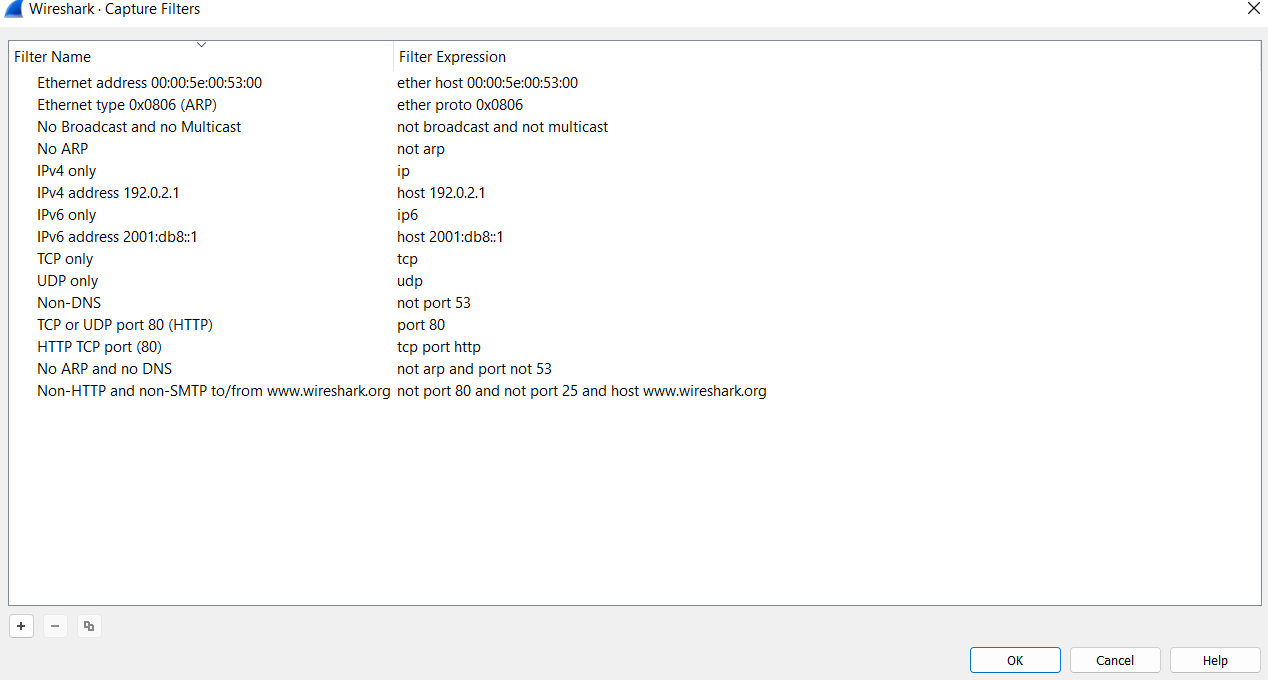
Capture Filter Syntax
These filters use byte offsets hex values and masks with boolean operators, and it is not easy to understand/predict the filter’s purpose at first glance. The base syntax is explained below:
- Scope: host, net, port and portrange.
- Direction: src, dst, src or dst, src and dst,
- Protocol: ether, wlan, ip, ip6, arp, rarp, tcp and udp.
- Sample filter to capture port 80 traffic:
tcp port 80
Capture filters
Display Filter Syntax
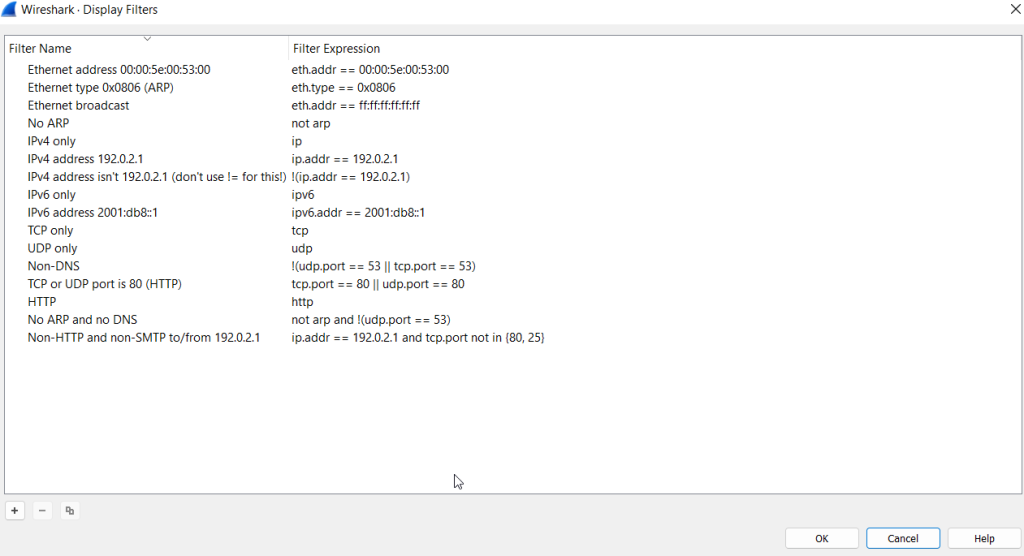
This is Wireshark’s most powerful feature. It supports 3000 protocols and allows conducting packet-level searches under the protocol breakdown. The official “Display Filter Reference” provides all supported protocols breakdown for filtering.
- Sample filter to capture port 80 traffic:
tcp.port == 80
Display filters
Comparison Operators
The primary operators are shown in the table below.
| English | C-Like | Description | Example |
| eq | == | Equal | ip.src == 10.10.10.100 |
| ne | != | Not equal | ip.src != 10.10.10.100 |
| gt | > | Greater than | ip.ttl > 250 |
| lt | < | Less Than | ip.ttl < 10 |
| ge | >= | Greater than or equal to | ip.ttl >= 0xFA |
| le | <= | Less than or equal to | ip.ttl <= 0xA |
Note: Wireshark supports decimal and hexadecimal values in filtering. You can use any format you want according to the search you will conduct.
Logical Expressions
Wireshark supports boolean syntax. You can create display filters by using logical operators as well.
| English | C-Like | Description | Example |
| and | && | Logical AND | (ip.src == 10.10.10.100) AND (ip.src == 10.10.10.111) |
| or | || | Logical OR | (ip.src == 10.10.10.100) OR (ip.src == 10.10.10.111) |
| not | ! | Logical NOT | !(ip.src == 10.10.10.222)Note: Usage of !=value is deprecated; using it could provide inconsistent results. Using the !(value) style is suggested for more consistent results. |
Packet Filter Toolbar
The filter toolbar is where you create and apply your display filters. It is a smart toolbar that helps you create valid display filters with ease. Before starting to filter packets, here are a few tips:
- Packet filters are defined in lowercase.
- Packet filters have an autocomplete feature to break down protocol details, and each detail is represented by a “dot”.
- Packet filters have a three-colour representation explained below.
Protocol Filters
As mentioned in the previous task, Wireshark supports 3000 protocols and allows packet-level investigation by filtering the protocol fields. This task shows the creation and usage of filters against different protocol fields.
IP Filters
IP filters help analysts filter the traffic according to the IP level information from the packets (Network layer of the OSI model). This is one of the most commonly used filters in Wireshark. These filters filter network-level information like IP addresses, version, time to live, type of service, flags, and checksum values.
The common filters are shown in the given table.
| Filter | Description |
ip | Show all IP packets. |
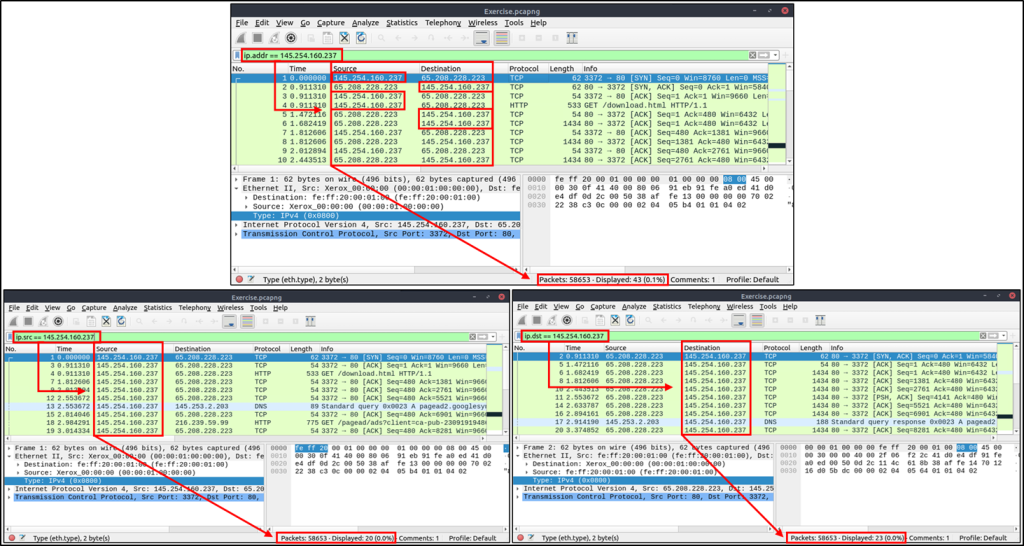
ip.addr == 10.10.10.111 | Show all packets containing IP address 10.10.10.111. |
ip.addr == 10.10.10.0/24 | Show all packets containing IP addresses from 10.10.10.0/24 subnet. |
ip.src == 10.10.10.111 | Show all packets originated from 10.10.10.111 |
ip.dst == 10.10.10.111 | Show all packets sent to 10.10.10.111 |
| ip.addr vs ip.src/ip.dst | Note: The ip.addr filters the traffic without considering the packet direction. The ip.src/ip.dst filters the packet depending on the packet direction. |
TCP and UDP Filters
TCP filters help analysts filter the traffic according to protocol-level information from the packets (Transport layer of the OSI model). These filters filter transport protocol level information like source and destination ports, sequence number, acknowledgement number, windows size, timestamps, flags, length and protocol errors.
| Filter | Description | Filter | Expression |
tcp.port == 80 | Show all TCP packets with port 80 | udp.port == 53 | Show all UDP packets with port 53 |
tcp.srcport == 1234 | Show all TCP packets originating from port 1234 | udp.srcport == 1234 | Show all UDP packets originating from port 1234 |
tcp.dstport == 80 | Show all TCP packets sent to port 80 | udp.dstport == 5353 | Show all UDP packets sent to port 5353 |

Application Level Protocol Filters | HTTP and DNS
Application-level protocol filters help analysts filter the traffic according to application protocol level information from the packets (Application layer of the OSI model ). These filters filter application-specific information, like payload and linked data, depending on the protocol type.
| Filter | Description | Filter | Description |
http | Show all HTTP packets | dns | Show all DNS packets |
http.response.code == 200 | Show all packets with HTTP response code “200” | dns.flags.response == 0 | Show all DNS requests |
http.request.method == "GET" | Show all HTTP GET requests | dns.flags.response == 1 | Show all DNS responses |
http.request.method == "POST" | Show all HTTP POST requests | dns.qry.type == 1 | Show all DNS “A” records |

Display Filter Expressions
As mentioned earlier, Wireshark has a built-in option (Display Filter Expression) that stores all supported protocol structures to help analysts create display filters. When an analyst can’t recall the required filter for a specific protocol or is unsure about the assignable values for a filter, the Display Filter Expressions menu provides an easy-to-use display filter builder guide. It is available under the “Analyse –> Display Filter Expression” menu.
It is impossible to memorise all details of the display filters for each protocol. Each protocol can have different fields and can accept various types of values. The Display Filter Expressions menu shows all protocol fields, accepted value types (integer or string) and predefined values (if any). Note that it will take time and require practice to master creating filters and learning the protocol filter fields.


