Installing Impacket:
As a First step, to clone the Impacket Github repo onto the KALI Linuxmachine. The following command will clone Impacket into /opt/impacket:
git clone https://github.com/SecureAuthCorp/impacket.git /opt/impacket
After the repo is cloned, verify the install related files, requirements.txt, and setup.py. Setup.py, this actually installs Impacket onto your system so you can use Impacket and not have to worry about any dependencies.
To install the Python requirements for Impacket:
pip3 install -r /opt/impacket/requirements.txt
Once the requirements have finished installing, then run the python setup install script:
cd /opt/impacket/ && python3 ./setup.py install
After that, Impacket should be correctly installed now and it should be ready to use!
Installing Bloodhound and Neo4j:
Bloodhound is another tool that will be utilised while attacking Active Directory. We can install it with the following command:
apt install bloodhound neo4j
AD Enumeration with Nmap:
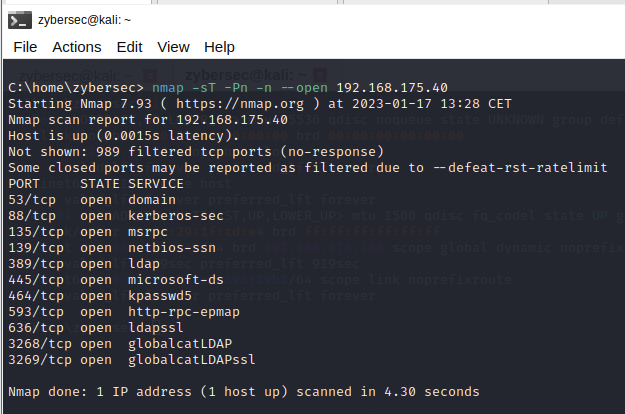
Basic enumeration starts out with an Nmap scan.
Nmap is a common choice for a port scan and for good reason, Nmap has tons of options and is capable of much more than simple port scanning.
A basic port scan using Nmap of the top 1000 TCP ports is shown:
Domain controllers are the most important systems in Microsoft Windows networks using the AD technology as they control all the machines in the network and host critical services for the organization’s operations such as DNS resolution. During a black-box penetration test, attackers need to locate these critical systems to examine them for possible vulnerabilities.
Enumerating the local network for the presence of a domain controller(DC)
Method 1: Scanning the local network for LDAP service
One method to locate the DCs is by searching for the LDAP service. LDAP usually runs on TCP port 389, and NSE has version detection signatures that can help us identify this service correctly.
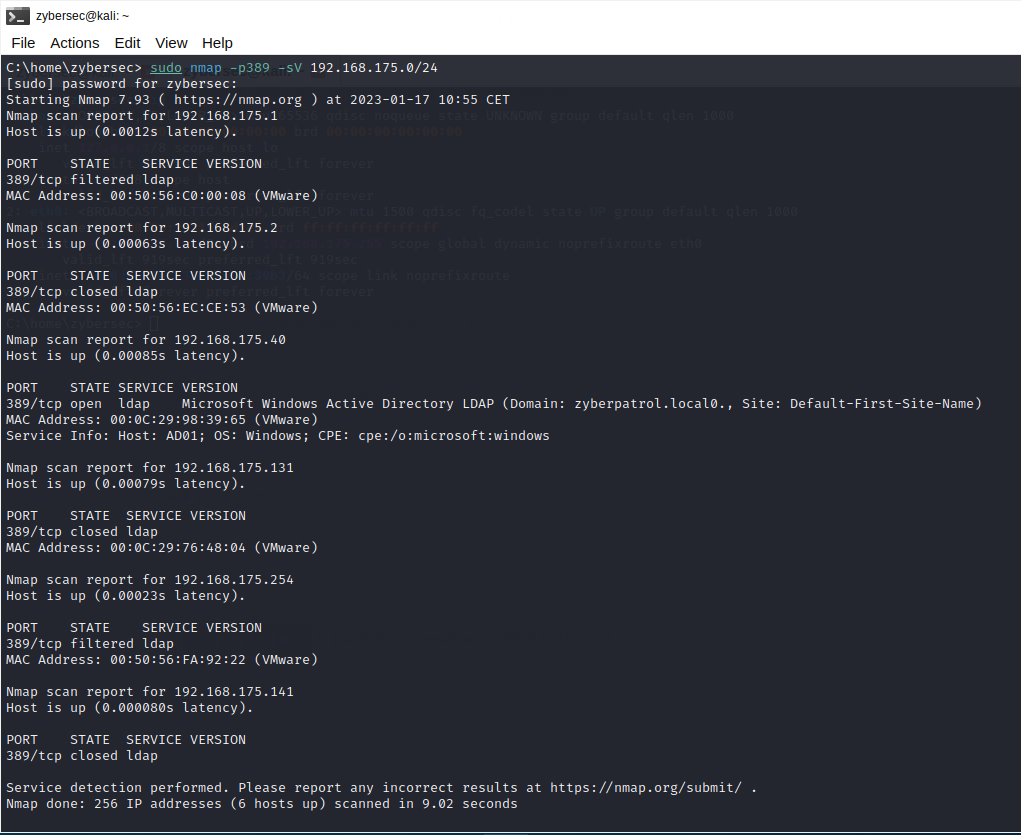
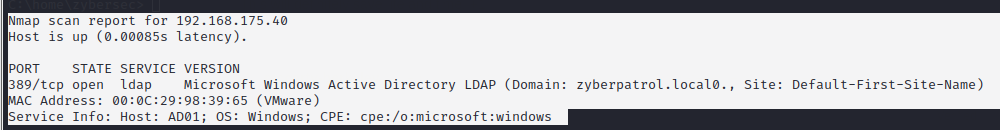
As per the above scan results, the host with the ip address 192.168.175.40 is running domain controller services for the AD domain zyberpatrol.local
Method 2: Finding domain master browsers