SMB(Server Message Block) Versions
Before diving into the various methods using to collect information from SMB, it is important to understand the iterations SMB went through over the years and why some of them are known to be highly insecure:
- SMB1 was the first implementation of SMB. It used 16-bit packet and small data buffers, which greatly limited performance, it did not have any encryption for data in transit whatsoever, which is why it is so insecure. In addition to this, it is highly susceptible to MITM (man-in-the-middle) attacks.
- SMB2 improved performance by increasing packets to 32-bit and 128-bit for files, furthermore unnecessary data that was transmitted when performing operating via SMB was substantially reduced. Security was improved to prevent MITM attacks through packet signing although still no built-in encryption support.
- SMB3 added more performance and security enhancements such as multichannel and end-to-end encryption using AES were introduced in, as well as functionality to enforce secure connections with newer clients.
Useful SMB Enumeration Tools
https://www.kali.org/tools/enum4linux/
https://www.kali.org/tools/smbmap/
https://github.com/SecureAuthCorp/impacket
https://github.com/Porchetta-Industries/CrackMapExec
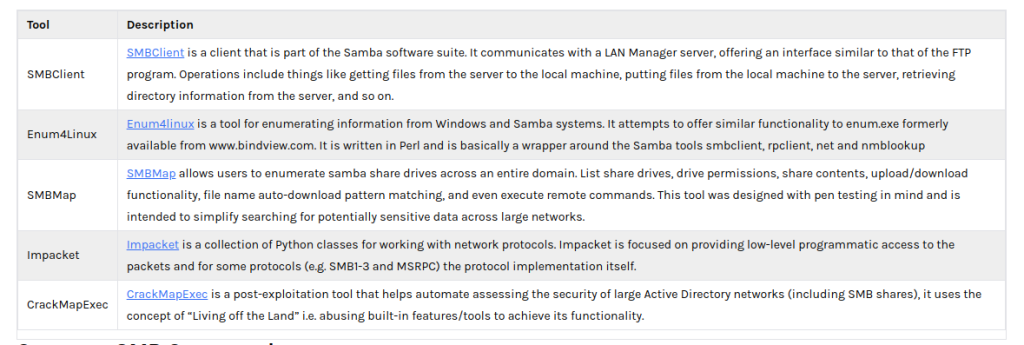
SMBCLIENT
smbclient is samba client with an “ftp like” interface. It is a useful tool to test connectivity to a Windows share. It can be used to transfer files, or to look at share names.
https://www.samba.org/samba/docs/current/man-html/smbclient.1.html
smbclient //mypc/myshare
To log in to a share: smbclient //IP/share -> you enter password and you are in
To copy local file to share: put test.txt -> you can add path details if the file is not in your local directory e.g /var/doc/test.txt
To copy file from share: get test.txt
Enumerating Files & Folders
smbclient [-U username] [-P password or -N for no password] \\\\X.X.X.X\\share
Enumerating Shares
smbclient [-U username] [-P password or -N for no password] -L \\\\X.X.X.X
Common SMB Commands
HYDRA – Bruteforcing Credentials
hydra [-L users.txt or -l user_name] [-P pass.txt or -p password] -f [-S port] ftp://X.X.X.X
NMAP commands:
nmap -p 139,445 X.X.X.X
nmap -p 139,445 -sV -Pn X.X.X.X → SMB/OS version detection
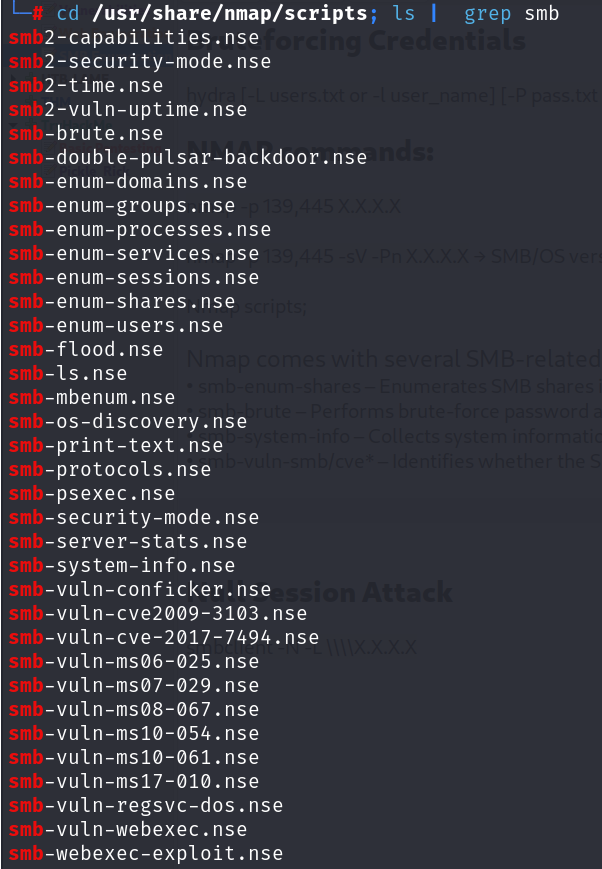
NMAP Scripts
Nmap comes with several SMB-related scripts such as:
- smb-enum-shares – Enumerates SMB shares in an SMB server.
- smb-brute – Performs brute-force password auditing against SMB servers.
- smb-system-info – Collects system information through SMB/NetBios.
- smb-vuln-smb/cve* – Identifies whether the SMB server is vulnerable to any known exploits.
nmap --script smb-os-discovery.nse -p445 <target>nmap --script smb-enum-shares.nse -p445 <target> nmap --script smb-enum-users.nse -p445 <target> nmap --script smb-vuln* 192.168.1.16 nmap --script smb-vuln-conficker.nse,smb-vuln-cve2009-3103.nse,smb-vuln-cve-2017-7494.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse,smb-vuln-regsvc-dos.nse,smb-vuln-webexec.nse -p445 <target>
Null Session Attack
smbclient -N -L \\\\X.X.X.X
SMBmap
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file name auto-download pattern matching, and even execute remote commands.
smbmap -H <IP> smbmap -u "user" -p "pass" -H <IP>
use NTLM hashes to authenticate
smbmap -u "username" -p "<NT>:<LM>" -H <IP>
Non Recursive listing
smbmap [-u "username" -p "password"] -r [Folder] -H <IP>
Recursive listing
smbmap [-u "username" -p "password"] -R [Folder] -H <IP>
File name search
sudo smbmap -R Folder -H <IP> -A <FileName> -q ()
Enum4Linux
enum4linux -A <target>
nbtscan
NetBIOS name discovery
nbtscan -r 192.168.0.1/24 nbtscan X.X.X.X nmap --script nbstat.nse X.X.X.X nbtstat -A X.X.X.X
Net view
Displays a list of domains, computers, or resources that are being shared by the specified computer.
net view \\192.168.1.17 /All
Metasploit
Metasploit: smb_enumshares
use auxiliary/scanner/smb/smb_enumshares set rhosts X.X.X.X smbuser xyz smbuser pass 123 exploit
CrackMapExec
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks.
crackmapexec smb X.X.X.X -u 'xyz' -p '123' --shares
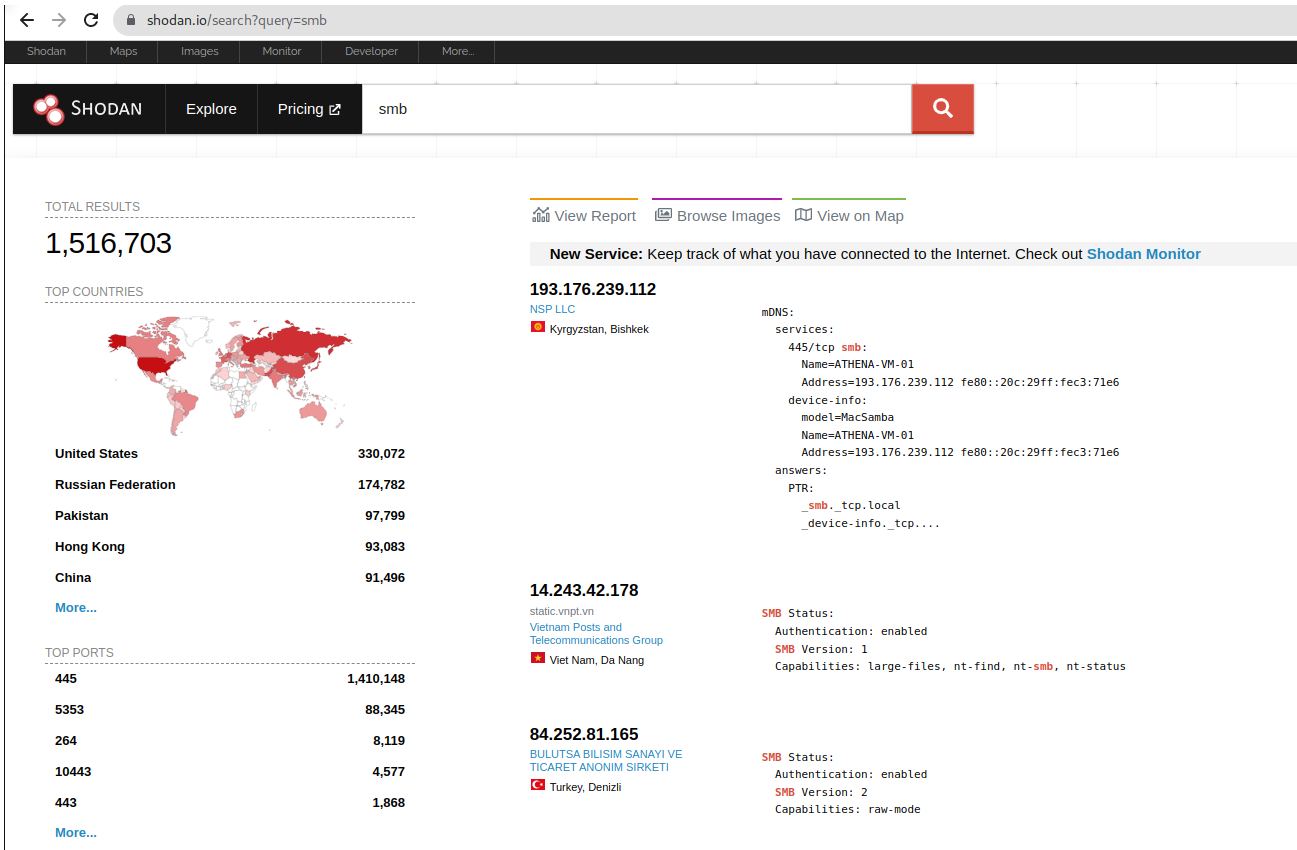
Shodan
A quick query in Shodan confirms that there are 1,516,703 publicly accessible SMB ports