Burp Suite
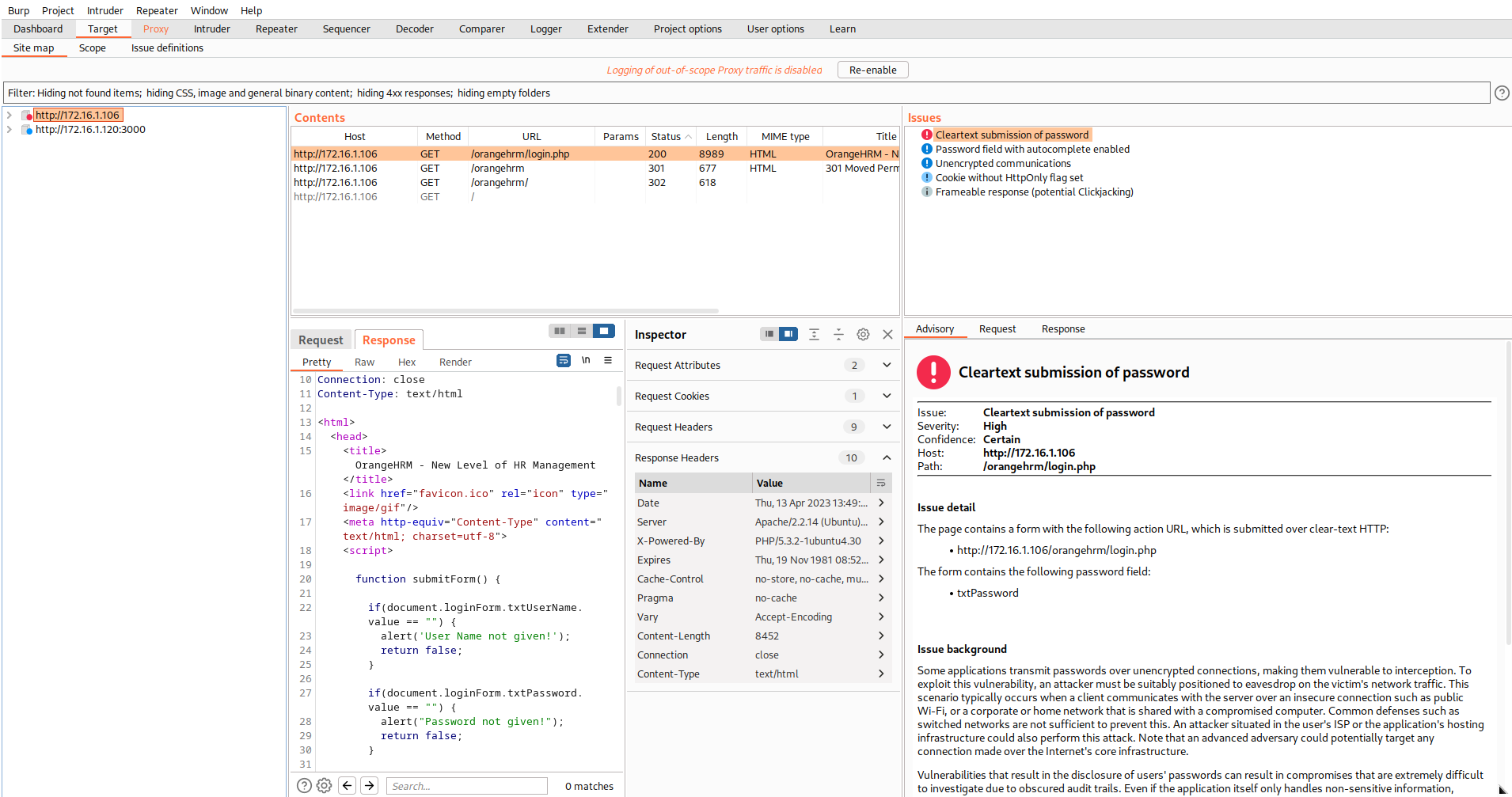
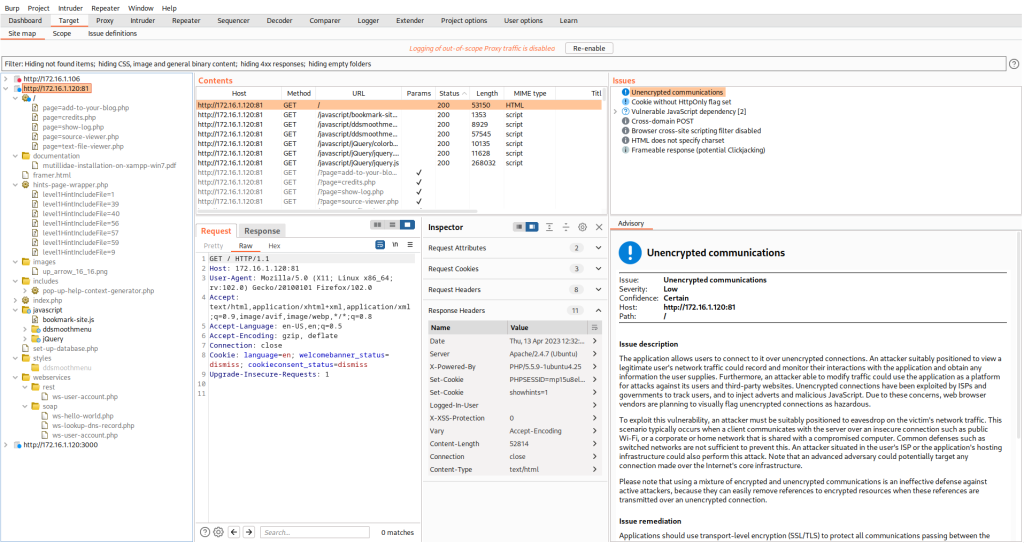
Target: This tool allows you to visualize your target application’s contents in a folder structure hierarchy that corresponds to the site’s URL structure. This section shows all of the content that has been is covered until now, by manually browsing the site’s pages.
Proxy: This is the main engine of Burp, which allows it to intercept and modify all web traffic.
Spider: This is a web spider tool that crawls applications to locate contents and functionalities.
Scanner: This tool is a web vulnerability scanner, which discovers numerous types of web vulnerabilities (SQLi, XSS, and CSRF) automatically. Scanner is available in the professional version only.
Intruder: This is a powerful tool for carrying out automated, customized attacks against web applications. I call it the web fuzzer; web fuzzing typically involves sending unexpected input to the target application. This process may help to identify web application security flaws.
Repeater: As the name suggests, it is used to manually modify and reissue web requests.
Sequencer: This analyzes the quality of randomness in an application’s session tokens or other important data items that are intended to be unpredictable.
Decoder: This allows for encoding and decoding data.
Comparer: The Burp Comparer is a handy utility for performing a visual differences between any two items of data, such as pairs of similar web responses.
Visualizing the target using Burp
Steps for WebApp Analysis
- Spider the web application branch
- Discover the hidden contents
- Inspect the web request/response of each page
- Passively scan the web application
- Actively scan the web application
- Perform some manual tests using the Intruder and Repeater tabs
- Test the vulnerabilities for false positives
- Generate a report
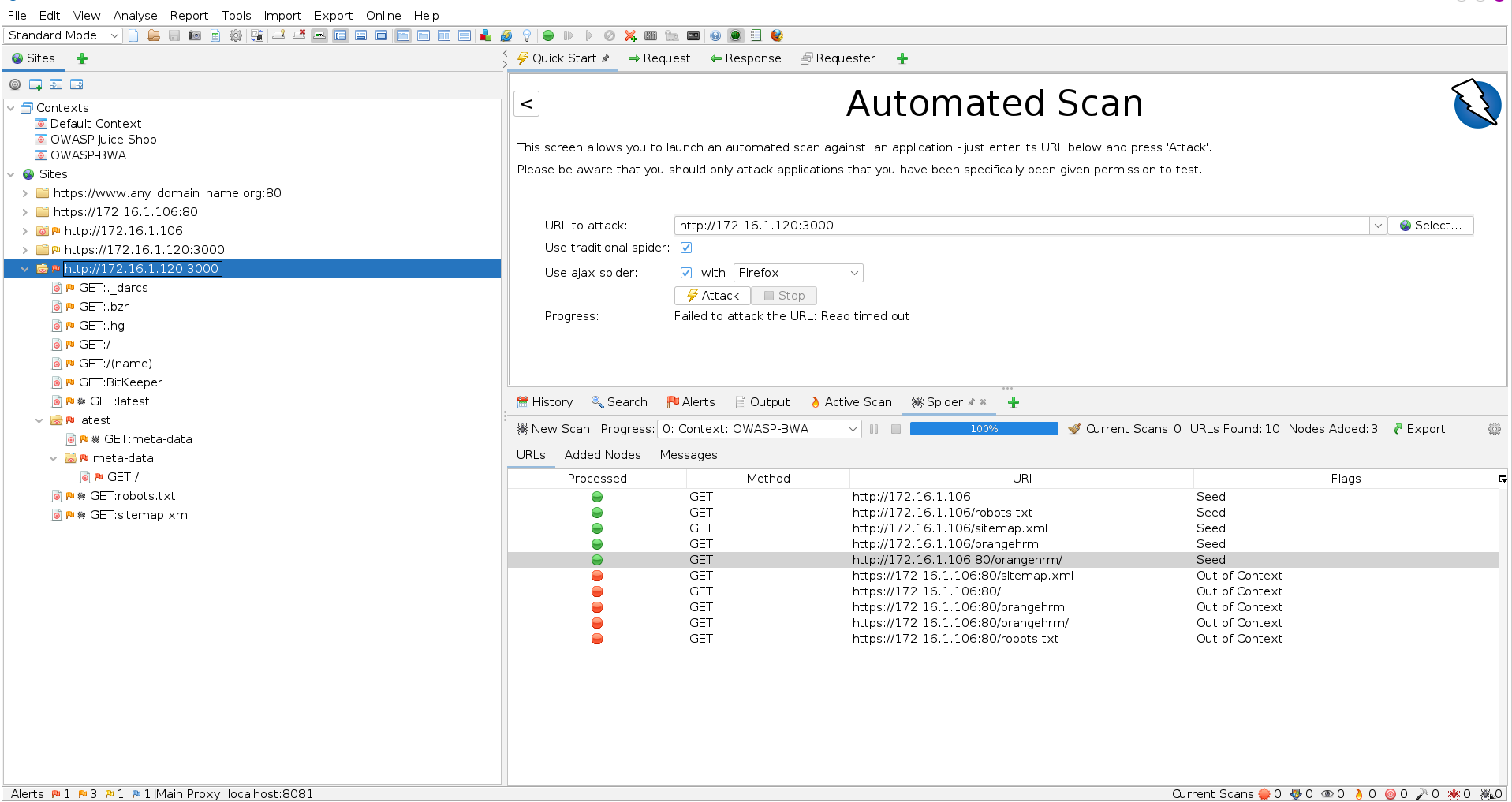
Crawling the WebApp using Burp Spider
OWASP ZAP