Dynamic Application Security Testing (DAST) is the process of testing a running instance of a web application for weaknesses and vulnerabilities. It focuses on a black-box testing approach where vulnerabilities are found just like a regular attacker would find them. Simply put, DAST identifies vulnerabilities by trying to exploit them, either manually or through automated tools.
It is important to note that DAST doesn’t replace other methods to find vulnerabilities in applications, but rather complements them. A secure development lifecycle will often mix several techniques in order to provide a good enough vulnerability coverage.
There are two ways in which DAST can be performed:
- Manual DAST: A security engineer will manually perform tests against an application to check for vulnerabilities.
- Automatic DAST: An automated tool will scan the web application for vulnerabilities.
Both processes are complementary and can be used at different stages of the Software Development Lifecycle (SDLC). Combining manual and automated tools will often yield the best results rather than relying on either separately.
Manual DAST will help us find weaknesses that an automated tool won’t easily spot as they don’t understand the application from a functional point of view.
The problem with doing everything by hand is that running manual tests for every commit or small change in the code during the development phases will take too much time. This is where Automated DAST excels, as it provides a quick way to run many tests against the target application without requiring human interaction.
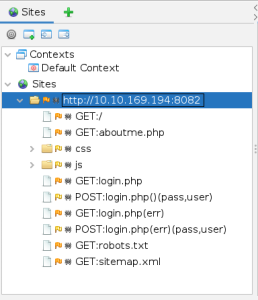
DAST in SDLC
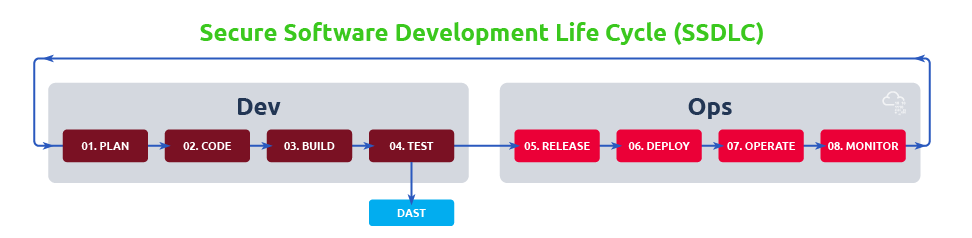
DAST Pros and Cons
DAST tool will perform at least the two following tasks against the target website:
- Spidering/Crawling: The tool will navigate through the web app, trying to map the application and identify a list of pages and parameters that can be attacked.
- Vulnerability Scanning: The tool will try to launch attack payloads against the identified pages and parameters. The user can typically customise the type of attacks to include only the ones relevant to the target application.
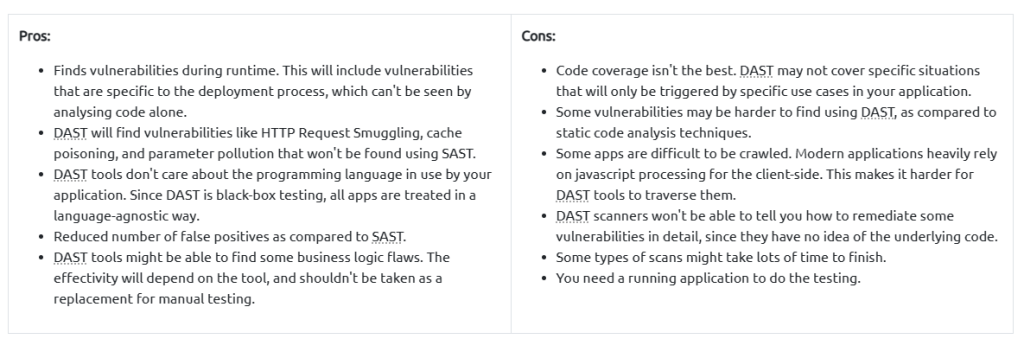
Spidering with ZAP
To spider a website, go to Tools -> Spider.
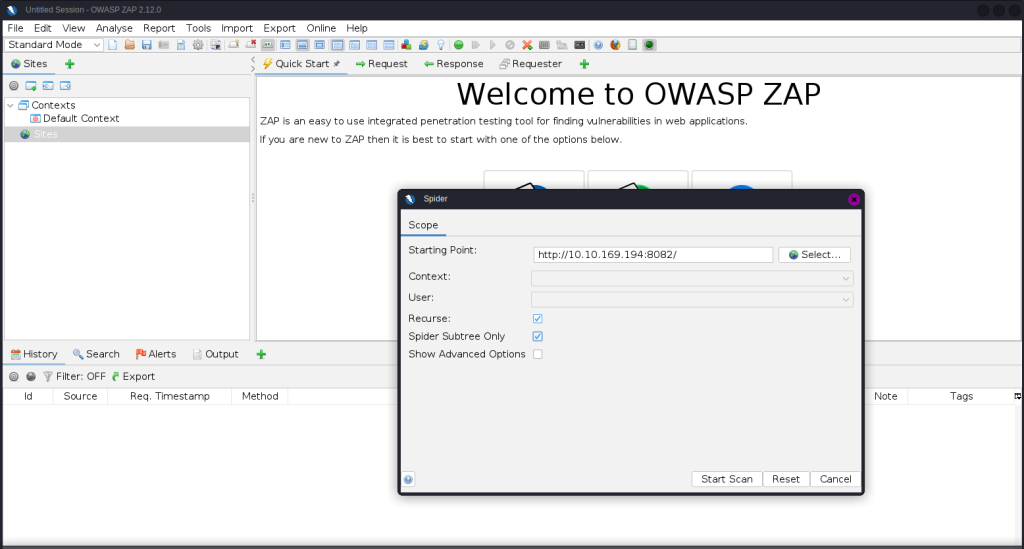
Spidering Result